Discover Cisco at a Glance: Supply Chain Operations
27:58
Cisco's purpose-driven supply chain organization, its strategic partnerships, and the roles and responsibilities of the supply chain team.
Related Videos
In Featured Video
-
Play video Back to Basics GenAI Webinar Series: What to do with data
Back to Basics GenAI Webinar Series: What to do with data
Explore how data pipelines are essential for any AI-driven application, and discover the foundational elements of data management, from collection to transformation to highlight their impact on the accuracy and effectiveness of GenAI Apps
58:29
-
Play video SheSpeaks+ Embracing a Lifelong Learning Mindset
SheSpeaks+ Embracing a Lifelong Learning Mindset
Join Marci Paino, VP of Enterprise Learning & Growth and Chief Learning Officer, for an engaging session on leadership development, career progression, and impactful experiential learning.
58:34
-
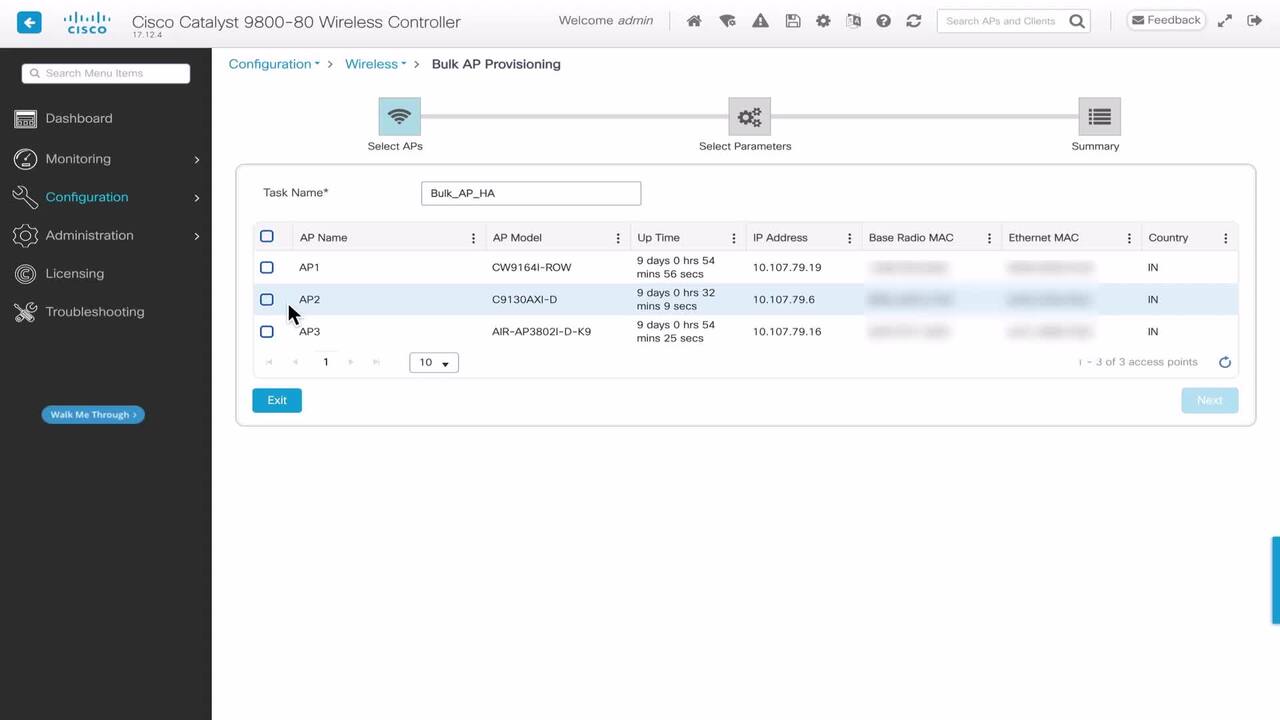
Play video Use Bulk AP Provisioning for High-Availability Configuration
Use Bulk AP Provisioning for High-Availability Configuration
This video demonstrates a configuration setup for Bulk AP Provisioning of High Availability Configuration on the C9800. Tags: Wireless, C9800
2:41
-
Play video DC Segmentation with VXLAN Group Policy Object (GPO) On-Demand Webinar
DC Segmentation with VXLAN Group Policy Object (GPO) On-Demand Webinar
Join this webinar to discover how you can implement segmentation on VXLAN EVPN fabrics with Nexus and the Group Policy Object (GPO) capabilities. Live demo included
1:34:26
-
Play video Unified management with Security Cloud Control
Unified management with Security Cloud Control
Hear Cisco Security CTO, Craig Connors explain how Security Cloud Control delivers unified management for Hybrid Mesh Firewall
2:23
-
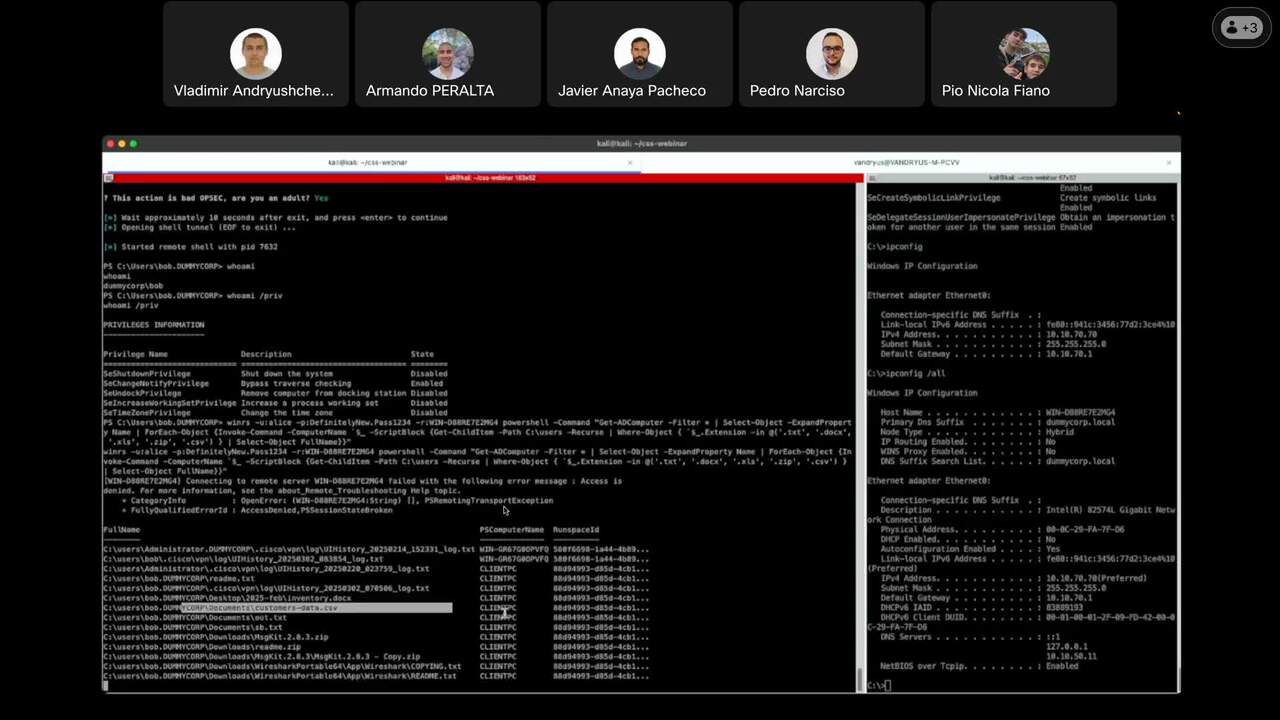
Play video Cybersecurity Threats Exposed: Real-World Attacks and Cisco Defenses
Cybersecurity Threats Exposed: Real-World Attacks and Cisco Defenses
Showcase of progression from an initial breach to full exploitation. Using real-world scenarios, illustration of the methods attackers use to infiltrate systems, exfiltrate data, and disrupt operations.
1:28:18