-
How network became an enabler of ambitions at Decathlon, the worldwide sports retailer
Decathlon needed a strong network player to support their fast developing activities. With their international footprint and rapid growth, they found that Cisco Meraki was the best solution to support their challenges and enable operations.
3:08
-
“It’s not about the technology itself. It’s about what the SMB customer is going to get out of it,” Craig Cieplinski, Cisco Global SMB Leader. Learn how Cisco partners are key to delivering the experience outcomes SMBs need.
It’s an exciting time in the SMB market. The SMB segment understands that technology is key to growth in their business. The biggest opportunity for partners is delivering SMBs the experience outcomes they can deliver with that technology.
24:22
-
Join Luxy Thuraisingam and Andrew Sage as they discuss the world of #CiscoSMB
Join Luxy Thuraisingam and Andrew Sage as they discuss the world of #CiscoSMB and share how we along with our #CiscoPartners deliver business outcomes for our #SMB customers. For access to exclusive partner content:http://cs.co/604158ORJ
7:39
-
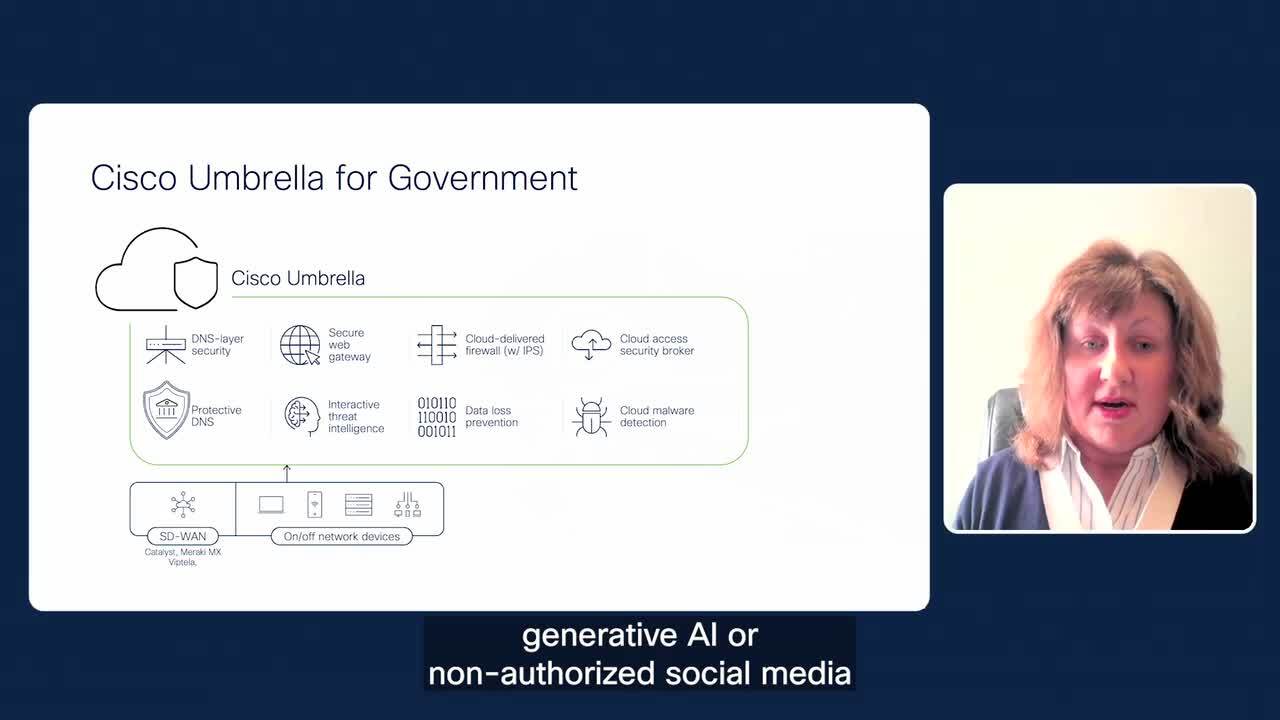
Cisco Umbrella for Government
Learn about cyber threat defense for government agencies to protect remote offices and hybrid workers.
2:19
-
Multicloud - Migrate Applications to Public Cloud
You want to migrate your apps to the public cloud to keep things simple. But it’s getting complicated, and it shouldn’t be.
0:48
-
Multicloud: Build and Manage a Hybrid Cloud
You need a hybrid cloud that gives you the functionality, efficiency, and security you require…and no tradeoffs.
0:51
-
Multicloud: Connect Branch Direct-to-Cloud - Lightboard
You need performance and security at your branches for your cloud applications and SaaS and for the user experience.
4:30
-
Cisco Container Platform: The Animated Overview
Need clarity on what Cisco Container Platform offers? This video outlines the value proposition in 1.5 minutes.
1:32
-
A Path to Success in the Cloud with Rackspace
Rackspace utilizes Cisco technology to provide expert managed services, ensuring customer success in AWS.
2:28
-
Multicloud Simplified
Cisco can help make cloud a great idea again with simplicity, security, and insights.
0:51
-
APIClarity Blog Series Introduction
This video introduces two new blog series on APIClarity: an overview series for the basics, and a how-to series to walk through the functionality.
1:46
-
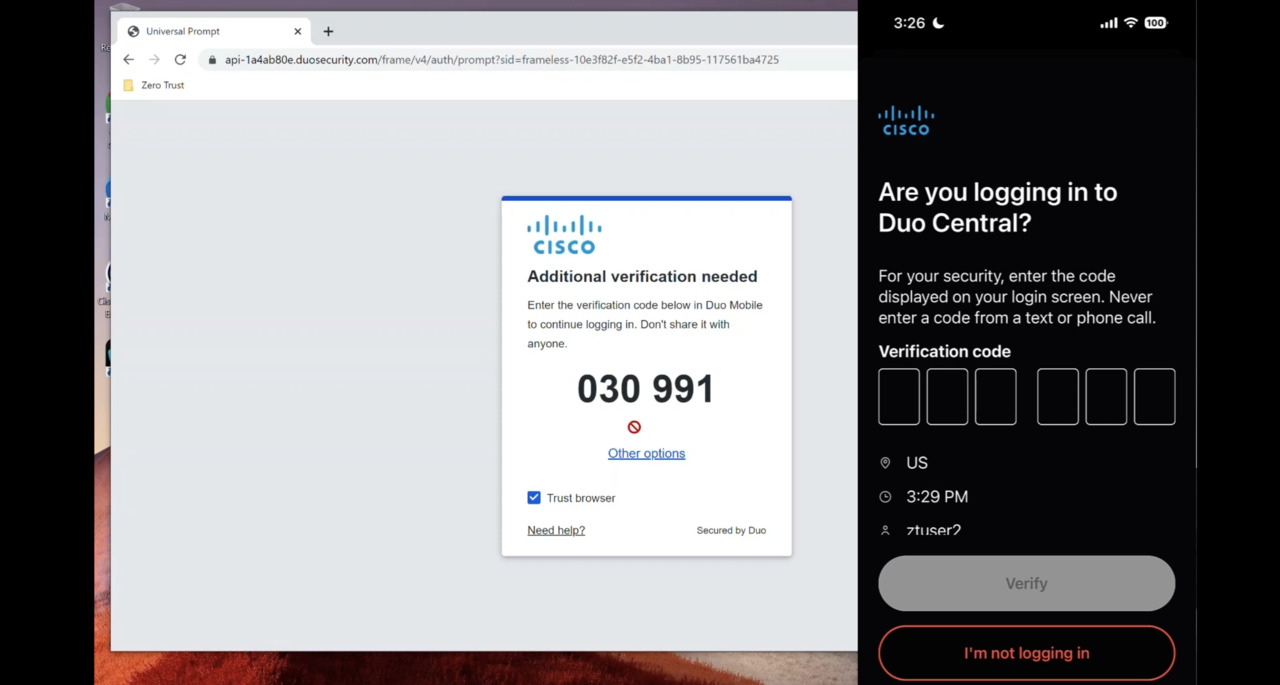
Cisco Zero Trust in Action: Secure user access to applications
This product demo shows a day in the life of a user gaining secure remote access to applications by continuously verifying user and device trust using Cisco zero trust technologies such as Duo and Umbrella.
7:40
- Load More
Cisco Video Portal


Share this video
Embed
Size: x pixels