-
The Power of the Platform: Cisco SASE
By integrating market-leading SD-WAN with cloud-native SSE, Cisco SASE delivers secure access in an optimized and orchestrated way. See each component working together - identifying and optimizing the best - and most secure - path for your business.
2:03
-
SASE for the AI Era from Cisco
Your organization can do amazing things with AI, if your network is ready for it. Cisco's SASE solution is designed to meet the new needs of the AI era - by identifying, optimizing, and securing AI traffic flows.
1:46
-
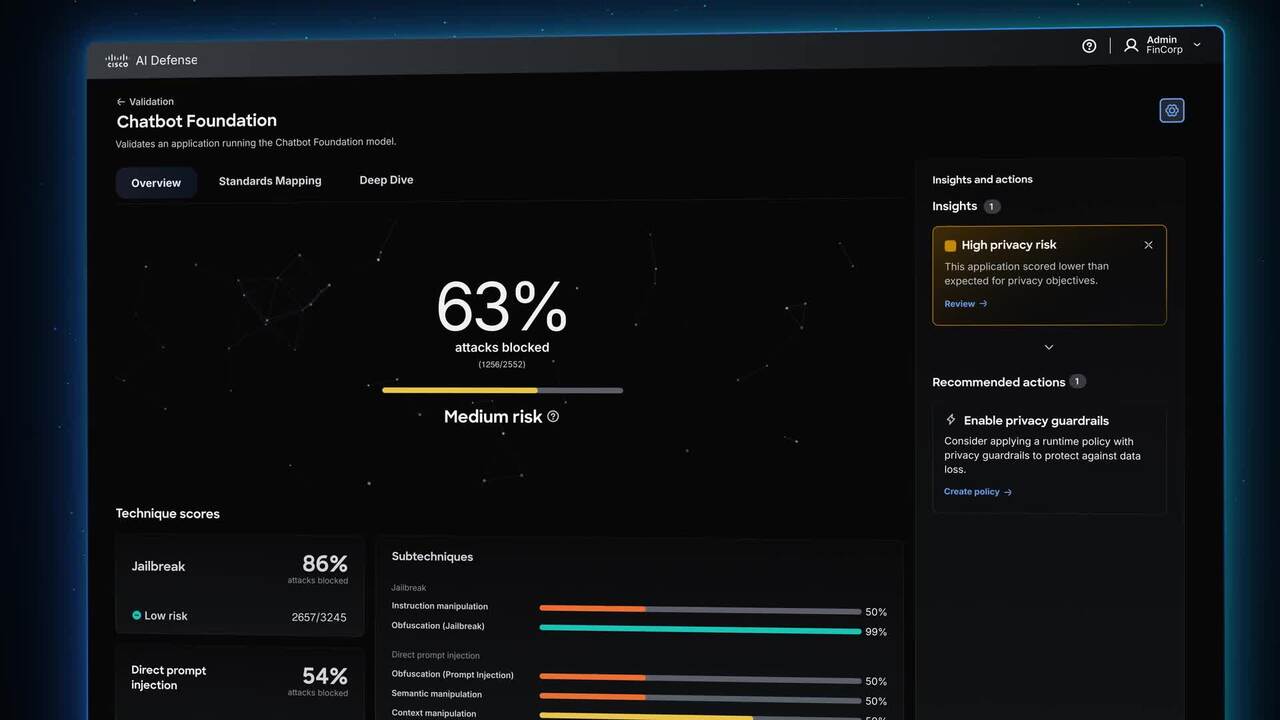
Meet Cisco AI Defense
Security built for the AI era. What stands between you and AI's promise is the unknown-new attack vectors, hidden AI assets, and risks traditional security can't see. Cisco AI Defense secures the AI lifecycle so teams can innovate with confidence.
2:19
-
Cisco Secure Firewall 6100 Series - Highest performance density for AI-ready data centers
The Cisco Secure Firewall 6100 Series is an ultra-high-end series firewall that protects AI-ready data centers and telecom mobility infrastructure with exceptional performance density, line-rate advanced threat protection, and modular scalability.
1:37
-
How Cisco’s Cutting-Edge Tech Keeps 70,000 49ers Fans Safe & Connected
49ers EVP Costa Kladianos explains why he trusts Cisco to power the team’s biggest NFL moments, including Super Bowl LX.
0:33
-
Secure Campus Overview Video
As AI is embedded into daily workflows, campus networks must be simpler to operate, secure by design, and built for real-time performance. Cisco Secure Campus achieves this with Agentic Operations, integrated security, and high-performance networking
2:15
-
Footholds in Infrastructure: Defending Service Providers from Cyberthreats
Discover the key cyberthreats targeting service providers, from espionage-driven advanced persistent threats (APTs) to silent intrusions and tough infrastructure decisions, and the risks they pose to critical networks.
2:36
-
AI-Ready Wireless Security: Integrating WPA3 & Beyond
Delve into AI-Ready Wireless Security: WPA3's evolution from WEP, its role in Wi-Fi 6E/7 (MLO, EHT), and enhanced cryptography. Covers holistic network security & emerging post-quantum cryptography to counter future threats.
18:53
-
The AI Ready Enterprise: Building a Secure Network Architecture for What's Next
Campus networks are under pressure— increased traffic, AI workloads, hybrid work, and a rising tide of IoT devices create unprecedented risks. Simplify and secure your AI-ready infrastructure with scalable, integrated security solutions to deliver a
2:22
-
Cisco Cyber Vision: Protecting OT at Scale
Get unparalleled visibility and threat detection across operational technology networks by analyzing industrial protocols and integrating with Cisco security products to secure OT environments at scale.
1:56
-
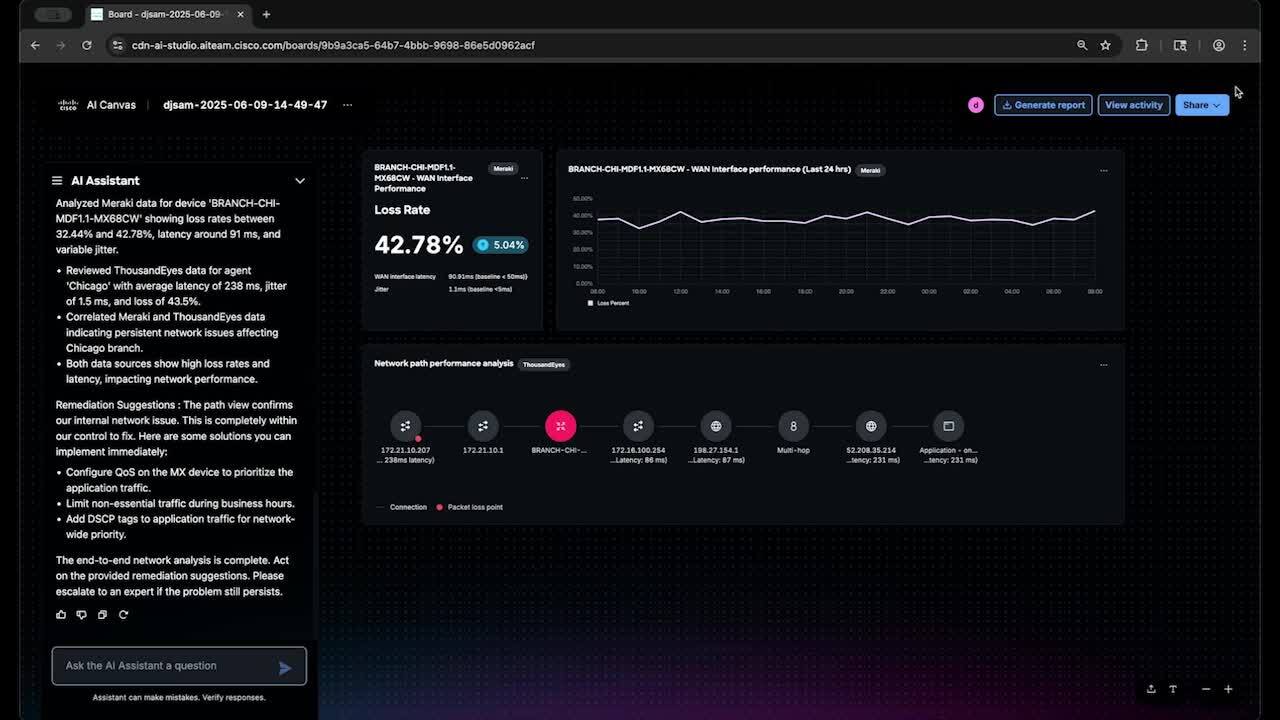
Introducing Cisco AI Canvas — The AgenticOps Revolution
AI Canvas is Cisco's first Generative UI for cross-domain IT-a shared, intelligent workspace that brings real-time telemetry, AI insights, and team collaboration into one view. Built for AgenticOps, it transforms how NetOps, SecOps, and app teams sol
6:26
-
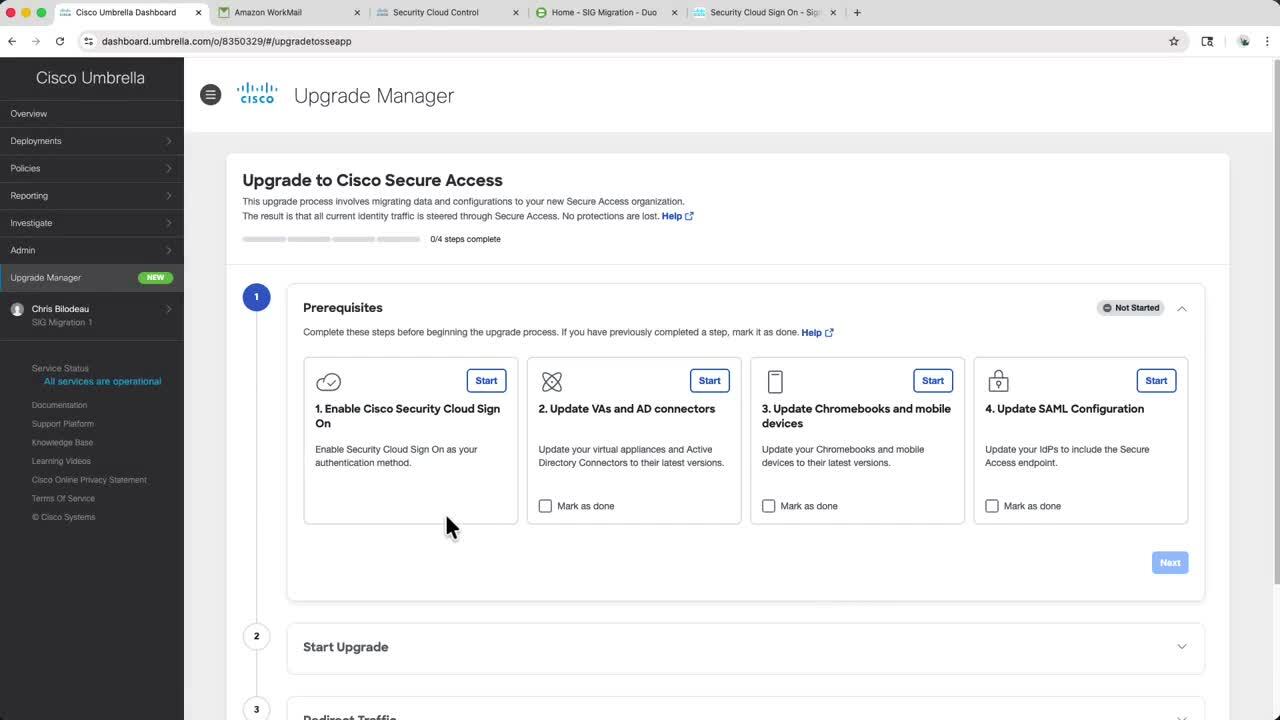
Moving to Cisco Secure Access: Cisco Umbrella SIG Migration Tutorial
Watch this video for a step-by-step guide of how to migrate from Cisco Umbrella SIG to Cisco Secure Access - Secure Internet Access (SIA) leveraging the automated upgrade manager.
8:28
- Load More
Cisco Video Portal


Share this video
Embed
Size: x pixels