Cisco Secure Firewall 200 Series Overview
1:05
The Cisco Secure Firewall 200 Series combines advanced NGFW with SD-WAN, delivering high-security branches with 3x better price-performance than similar firewalls.
Related Videos
In Security
-
Play video Cisco Hybrid Mesh Firewall - Hypershield
Cisco Hybrid Mesh Firewall - Hypershield
Protect your applications wherever they live This highly distributed security fabric with unified management is optimized for zero-trust segmentation and application protection in data center, cloud, campus, and IoT environments.
1:57
-
Play video Unlock Advanced Protection: Migrate from Cisco Umbrella to Cisco Secure Access
Unlock Advanced Protection: Migrate from Cisco Umbrella to Cisco Secure Access
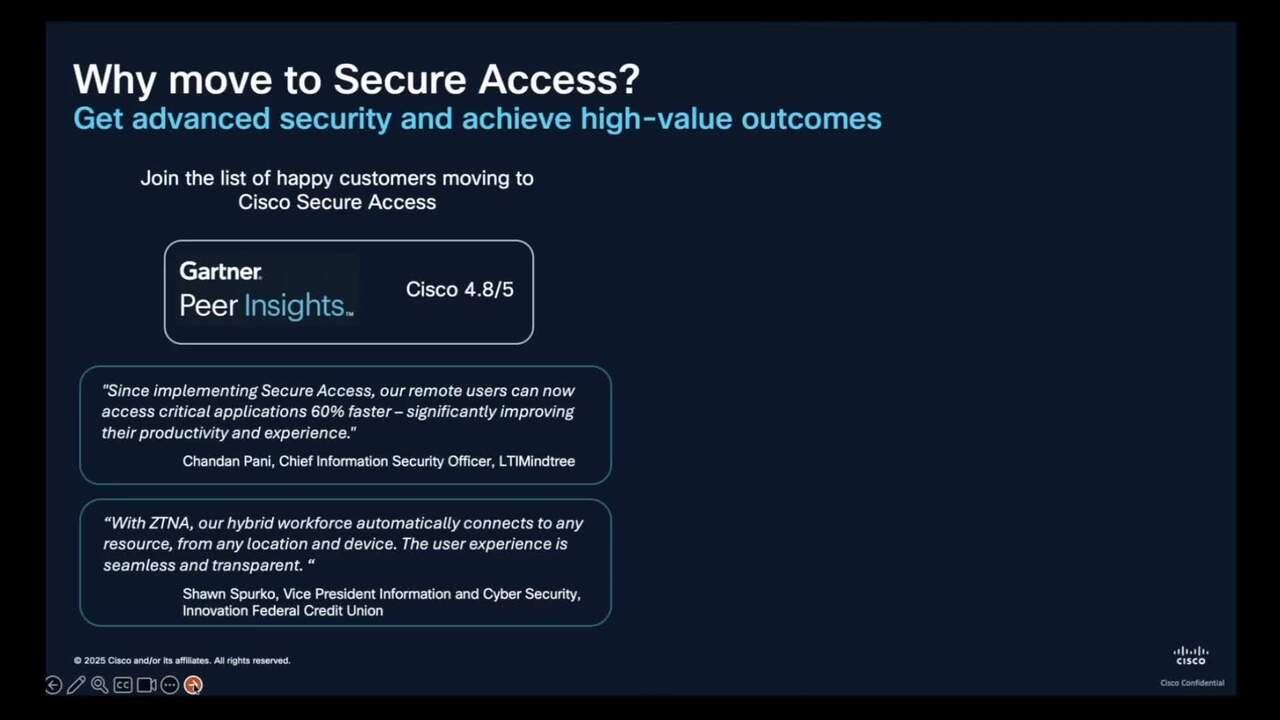
Watch this video for a breakdown of the top 5 reasons why you should migrate to Secure Access.
14:26
-
Play video Securing the Skies: How Wipro Safegaurds a Leading Airline
Securing the Skies: How Wipro Safegaurds a Leading Airline
Watch this aviation success story video on how Wipro, Cisco Secure Access and Google Chrome Enterprise Premium work together to deliver a secure way to access private applications from anywhere.
2:36
-
Play video Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods partnered with Cisco to modernize security by replacing legacy systems with a secure access service edge (SASE) framework. The company's goals are to unify networking and security, enable zero trust and streamline management.
2:55
-
Play video Cisco SASE: End-to-end. Everywhere.
Cisco SASE: End-to-end. Everywhere.
This video shows how Cisco SASE unifies network architecture and security policy, optimizing user experience and IT efficiency to accelerate zero trust security.
1:05
-
Play video Universal ZTNA from Cisco: Zero Friction. Zero Imposters. Zero Downtime.
Universal ZTNA from Cisco: Zero Friction. Zero Imposters. Zero Downtime.
Today, zero trust is the new normal. You get the least access to get the job done; nothing more. It sounds easy, but it’s not. Users and things are everywhere. Accessing sensitive assets, on any device, from anywhere. But so are attackers.
1:40