Cisco Secure Endpoint and Umbrella Use Cases Part 2
2:31
This scenario discusses a remediation use case of how we disconnect an endpoint from the network after Umbrella blocks malicious traffic.
Related Videos
In User & Endpoint Protection
-
Play video Alphabet Soup: Making Sense of EDR, MEDR, MDR, XDR
Alphabet Soup: Making Sense of EDR, MEDR, MDR, XDR
There are so many acronyms – EDR, MEDR, MDR, XDR, and more – when it comes to cybersecurity, making it harder to choose the right solution for your organization. Join Nirav Shah in this webinar to better understand these solutions.
12:15
-
Play video Secure MDR for Endpoint: Fireside Chat with Andy Hagar and Truman Coburn
Secure MDR for Endpoint: Fireside Chat with Andy Hagar and Truman Coburn
Join Cisco Secure Endpoint Product Marketing Manager Truman Coburn and Security Consulting Engineer Andy Hagar as they discuss the role Cisco Managed Detection and Response (MDR) Platform and Automation play when investigating and mitigating threats.
8:37
-
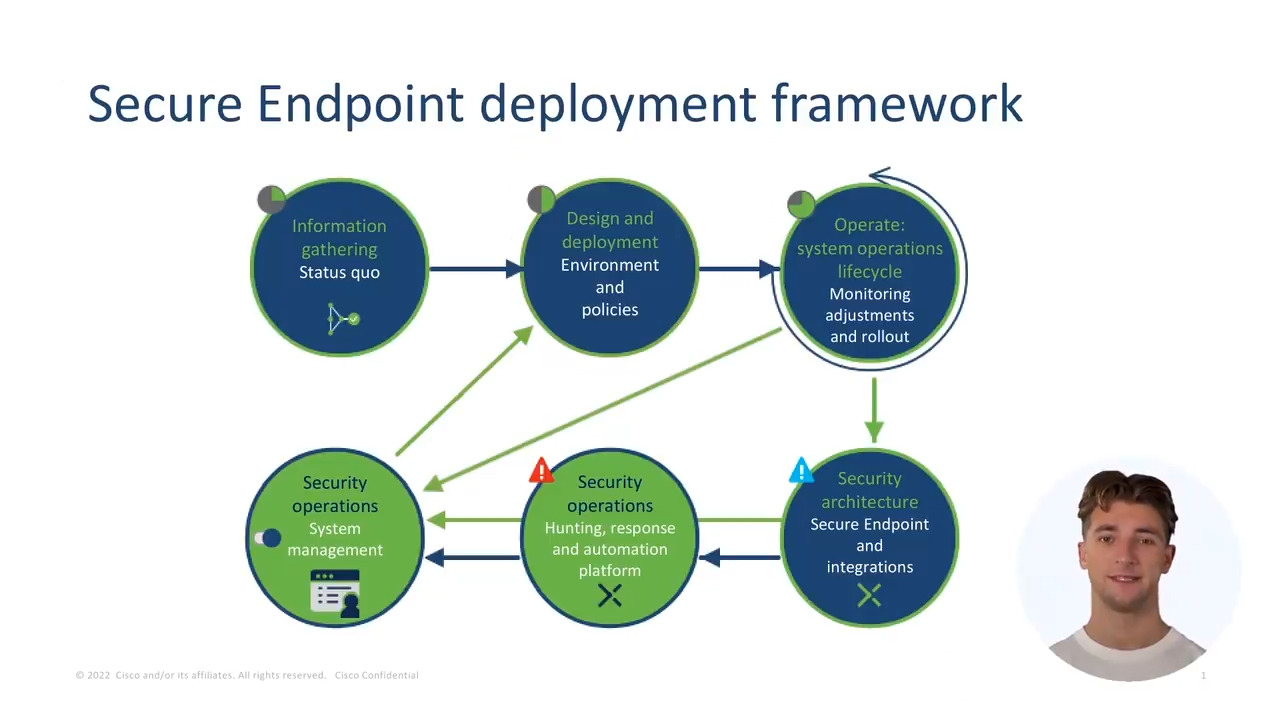
Play video Expanding connector deployment for Cisco Secure Endpoint
Expanding connector deployment for Cisco Secure Endpoint
This video will walk you through Cisco's framework for expanding connector deployment. It will help you understand and gather the information needed to roll out Cisco Secure Endpoint successfully. To learn more, view the article on Cisco Community
6:25
-
Play video Cisco Secure Endpoint Explainer Video
Cisco Secure Endpoint Explainer Video
Learn how Cisco Secure Endpoint does more than any other endpoint solution by unifying user and endpoint protection, with SecureX built-in.
1:37
-
Play video Cisco Secure Endpoint Explainer video with Tiers
Cisco Secure Endpoint Explainer video with Tiers
Learn how Cisco Secure Endpoint does more than any other endpoint solution by unifying user and endpoint protection, with SecureX built-in.
1:53
-
Play video What is Managed Security: Fireside Chat with Tuan Huyn and Truman Coburn
What is Managed Security: Fireside Chat with Tuan Huyn and Truman Coburn
Join Tuan Huyn, Engineering Leader, and Truman Coburn, Cisco Secure Endpoint Product Marketing Manager, in this fireside chat to learn about managed security.
11:44