Build resilience
0:32
Unlock end-to-end visibility from edge to app for faster troubleshooting. Expand your zero trust reach confidently with a unified approach.
Related Videos
In Security
-
Play video Birla Opus Paints - Connected Factories, Smarter Paint
Birla Opus Paints - Connected Factories, Smarter Paint
Birla Opus Paints built six new factories with one digital backbone, achieving speed, security, and resilience through Cisco-powered connected operations.
1:47
-
Play video Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods partnered with Cisco to modernize security by replacing legacy systems with a secure access service edge (SASE) framework. The company's goals are to unify networking and security, enable zero trust and streamline management.
2:55
-
Play video AI-Ready Wireless Security: Integrating WPA3 & Beyond
AI-Ready Wireless Security: Integrating WPA3 & Beyond
Delve into AI-Ready Wireless Security: WPA3's evolution from WEP, its role in Wi-Fi 6E/7 (MLO, EHT), and enhanced cryptography. Covers holistic network security & emerging post-quantum cryptography to counter future threats.
18:53
-
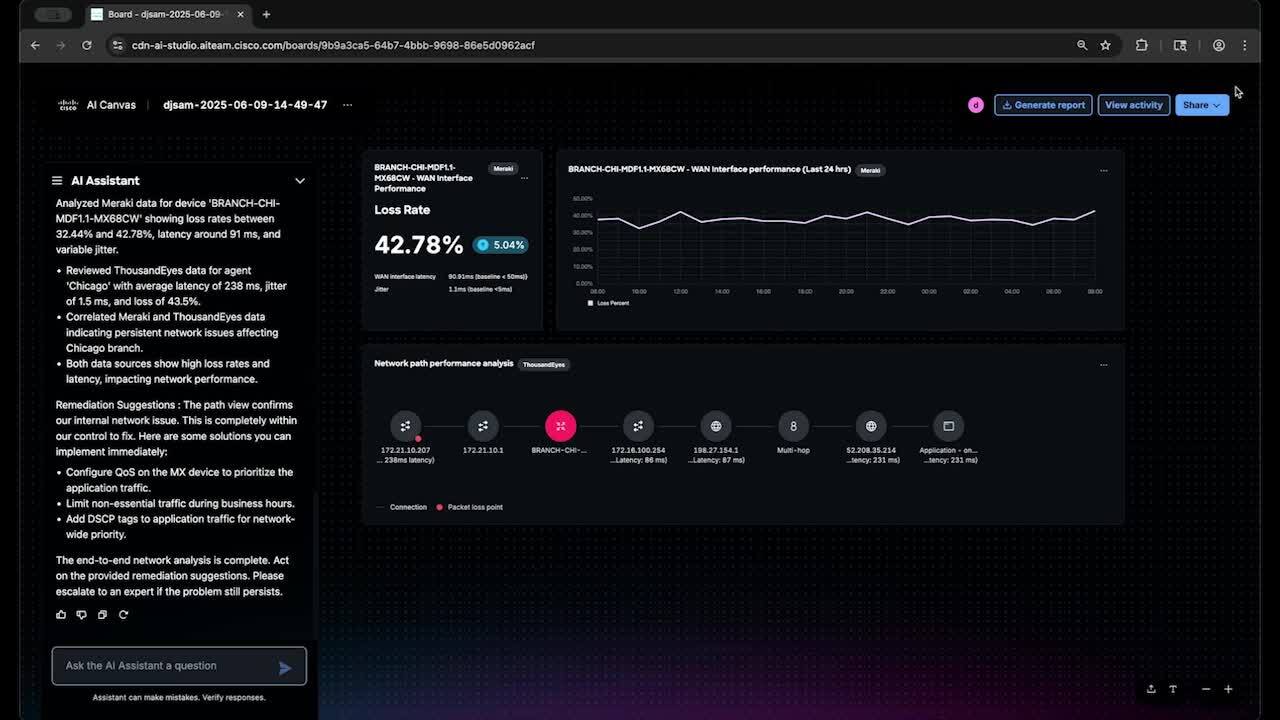
Play video Introducing Cisco AI Canvas — The AgenticOps Revolution
Introducing Cisco AI Canvas — The AgenticOps Revolution
AI Canvas is Cisco's first Generative UI for cross-domain IT-a shared, intelligent workspace that brings real-time telemetry, AI insights, and team collaboration into one view. Built for AgenticOps, it transforms how NetOps, SecOps, and app teams sol
6:26
-
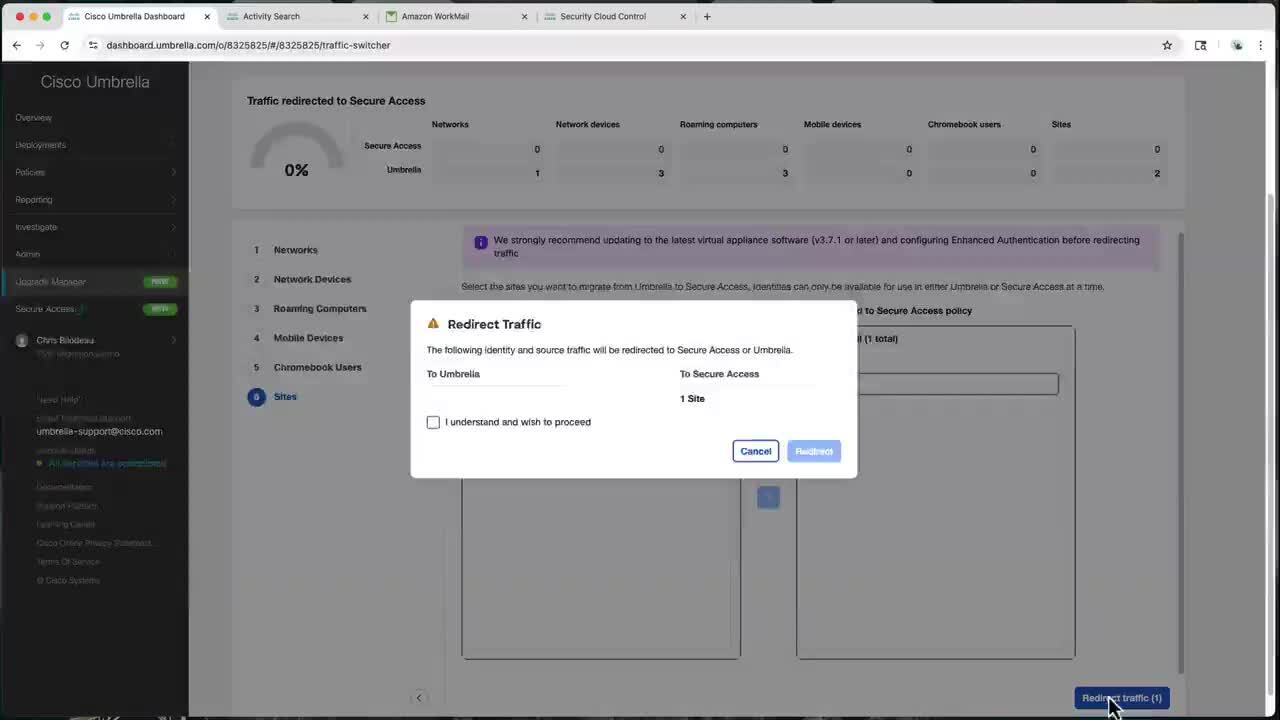
Play video Moving to Cisco Secure Access: Cisco Umbrella DNS Migration Tutorial
Moving to Cisco Secure Access: Cisco Umbrella DNS Migration Tutorial
Watch this brief video for a step-by-step guide for how to migrate from Cisco Umbrella DNS to Cisco Secure Access - DNS Defense using the automated upgrade manager.
12:22
-
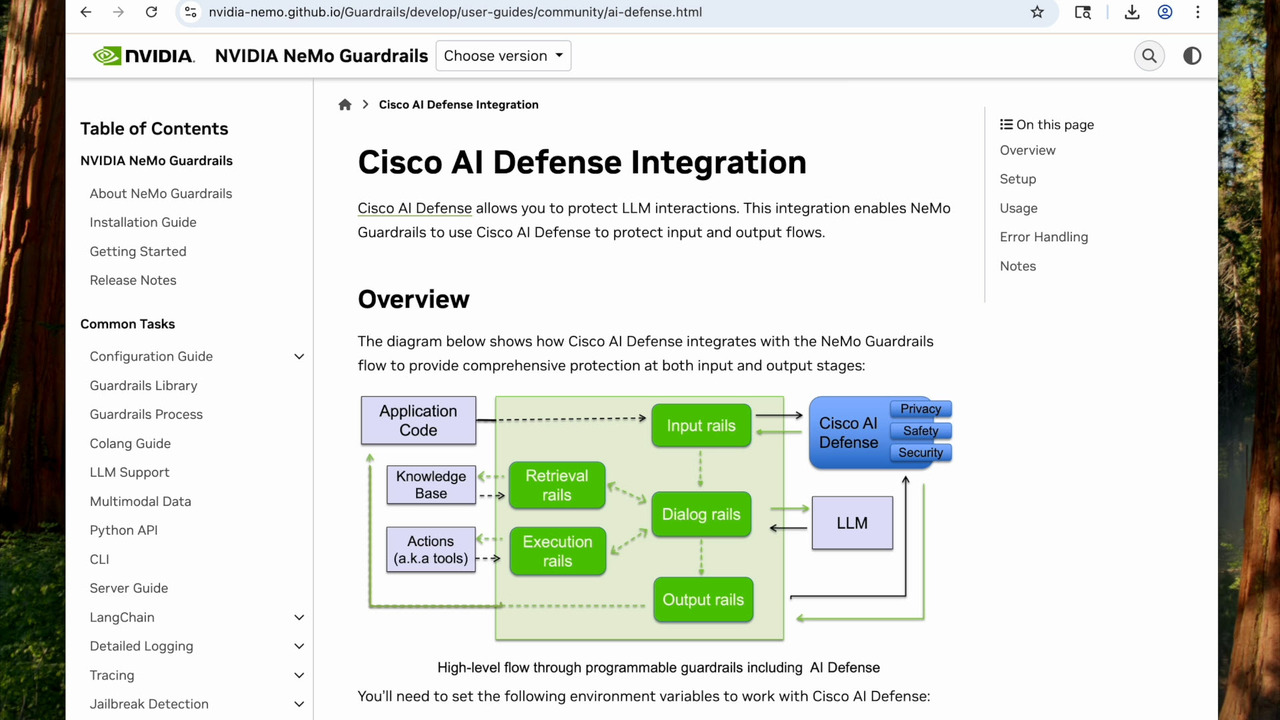
Play video Cisco AI Defense Integrates with NVIDIA Enterprise AI Software to Deliver Robust Cybersecurity for AI Applications Using NVIDIA NeMo Guardrails
Cisco AI Defense Integrates with NVIDIA Enterprise AI Software to Deliver Robust Cybersecurity for AI Applications Using NVIDIA NeMo Guardrails
See Cisco AI Defense in action with NVIDIA NeMo Guardrails, delivering real-time protection for AI applications.
3:51