Cisco XDR Detection Analytics and Gen AI
32:35
In this session, our experts unpack the sophisticated mechanisms behind Cisco XDR's ability to swiftly detect and correlate threats.
Related Videos
In Security
-
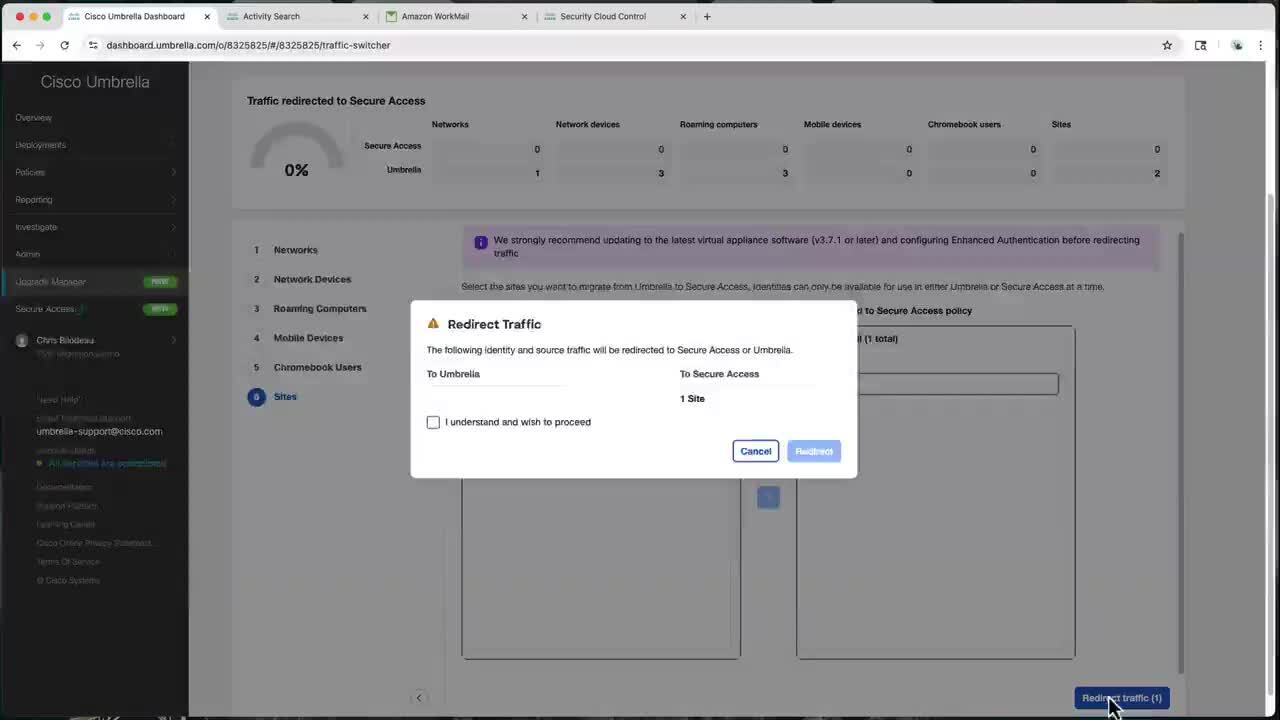
Play video Moving to Cisco Secure Access: Cisco Umbrella DNS Migration Tutorial
Moving to Cisco Secure Access: Cisco Umbrella DNS Migration Tutorial
Watch this brief video for a step-by-step guide for how to migrate from Cisco Umbrella DNS to Cisco Secure Access - DNS Defense using the automated upgrade manager.
12:22
-
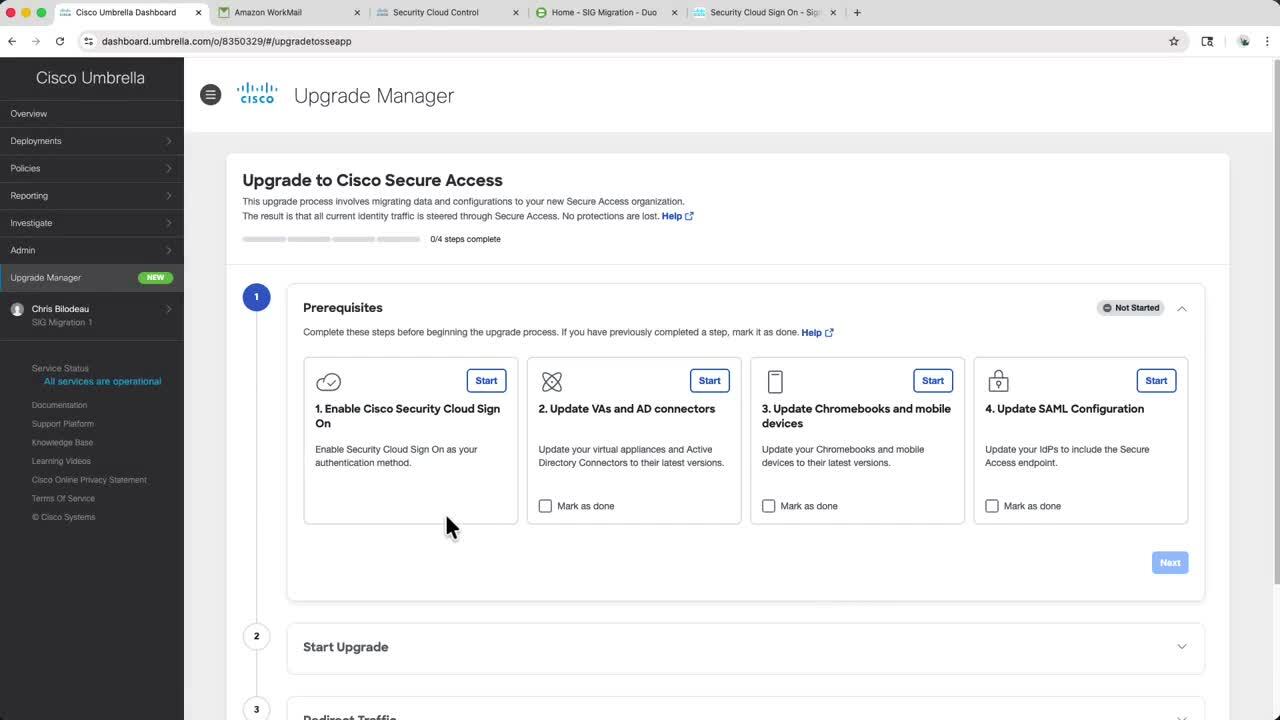
Play video Moving to Cisco Secure Access: Cisco Umbrella SIG Migration Tutorial
Moving to Cisco Secure Access: Cisco Umbrella SIG Migration Tutorial
Watch this video for a step-by-step guide of how to migrate from Cisco Umbrella SIG to Cisco Secure Access - Secure Internet Access (SIA) leveraging the automated upgrade manager.
8:28
-
Play video The AI Ready Enterprise: Building a Secure Network Architecture for What's Next
The AI Ready Enterprise: Building a Secure Network Architecture for What's Next
Campus networks are under pressure— increased traffic, AI workloads, hybrid work, and a rising tide of IoT devices create unprecedented risks. Simplify and secure your AI-ready infrastructure with scalable, integrated security solutions to deliver a
2:22
-
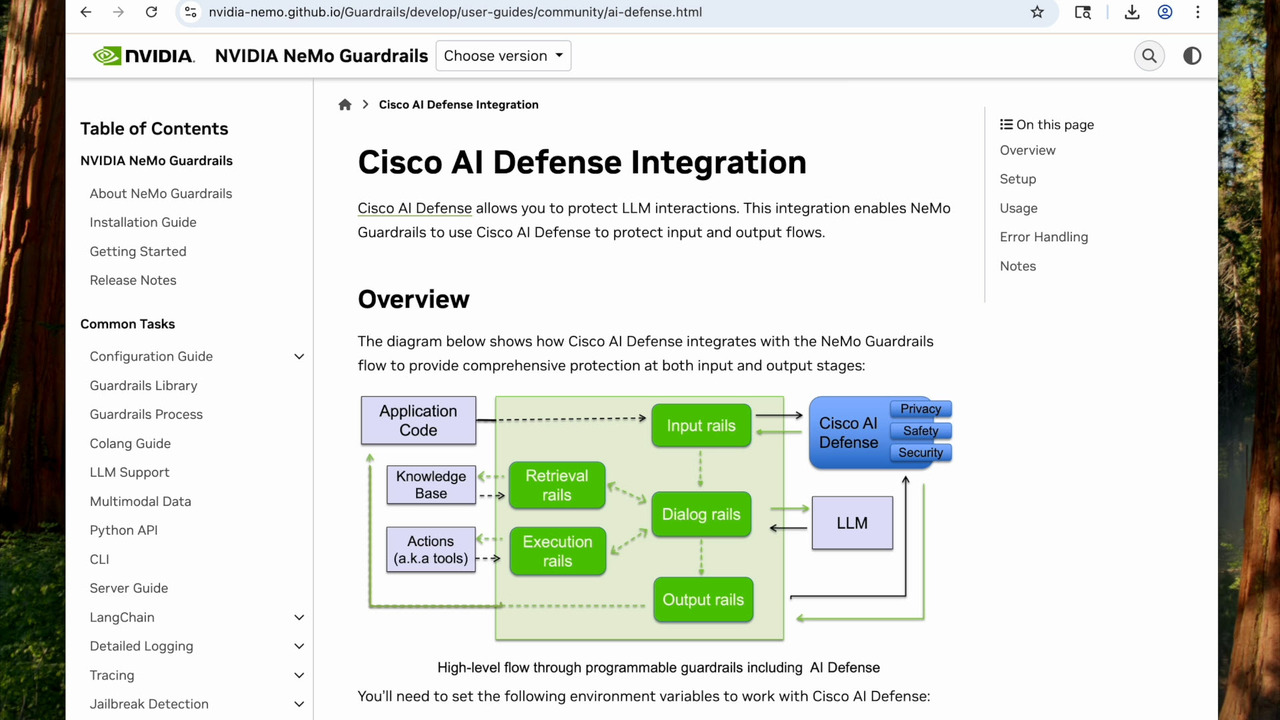
Play video Cisco AI Defense Integrates with NVIDIA Enterprise AI Software to Deliver Robust Cybersecurity for AI Applications Using NVIDIA NeMo Guardrails
Cisco AI Defense Integrates with NVIDIA Enterprise AI Software to Deliver Robust Cybersecurity for AI Applications Using NVIDIA NeMo Guardrails
See Cisco AI Defense in action with NVIDIA NeMo Guardrails, delivering real-time protection for AI applications.
3:51
-
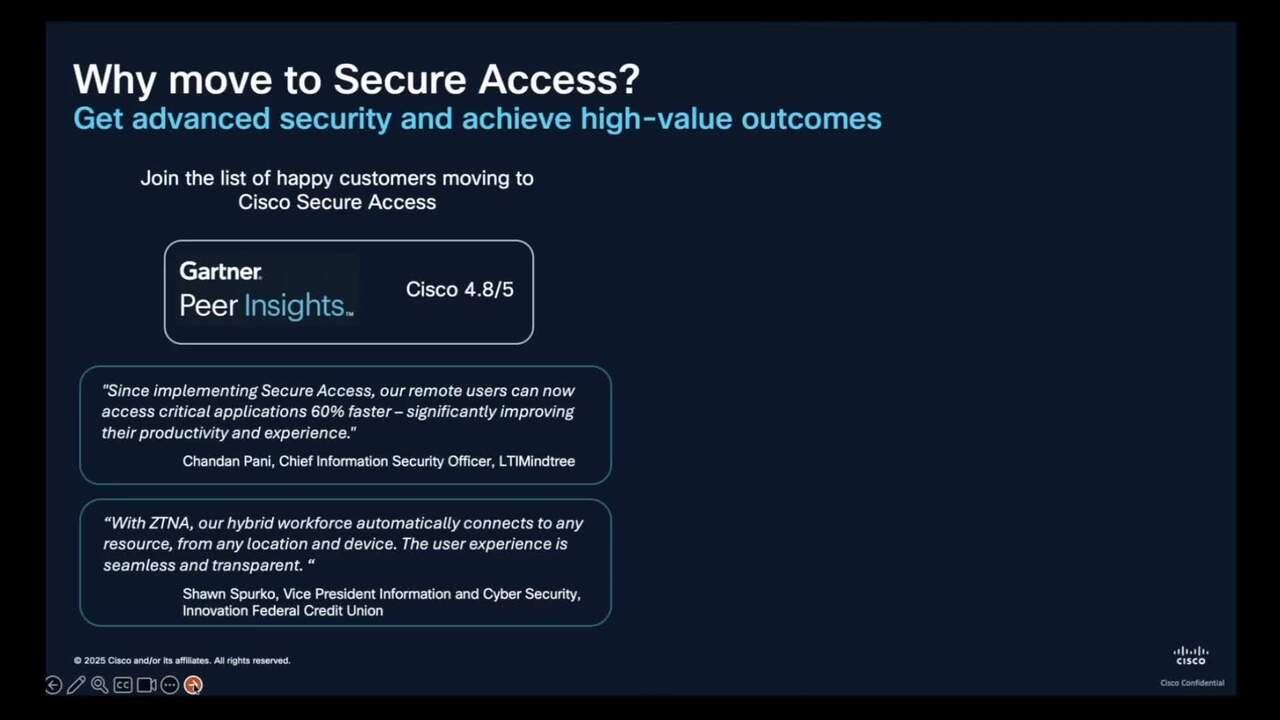
Play video Unlock Advanced Protection: Migrate from Cisco Umbrella to Cisco Secure Access
Unlock Advanced Protection: Migrate from Cisco Umbrella to Cisco Secure Access
Watch this video for a breakdown of the top 5 reasons why you should migrate to Secure Access.
14:26
-
Play video Introducing Cisco AI Canvas — The AgenticOps Revolution
Introducing Cisco AI Canvas — The AgenticOps Revolution
AI Canvas is Cisco's first Generative UI for cross-domain IT-a shared, intelligent workspace that brings real-time telemetry, AI insights, and team collaboration into one view. Built for AgenticOps, it transforms how NetOps, SecOps, and app teams sol
6:26