Cisco Security Leadership Workshop Q&A - Abhishek Kumar
9:57
Abhishek Kumar, CISO Advisory, Cisco EMEA, discusses the benefits of our two day Cisco Security Leadership Workshop.
Related Videos
In Security
-
Play video Protect identities
Protect identities
Discover accounts that may be at risk, or pose a risk. Use phishing-resistant multi-factor authentication (MFA) on all apps—legacy and modern ones—in a way that frustrates attackers and not users.
0:31
-
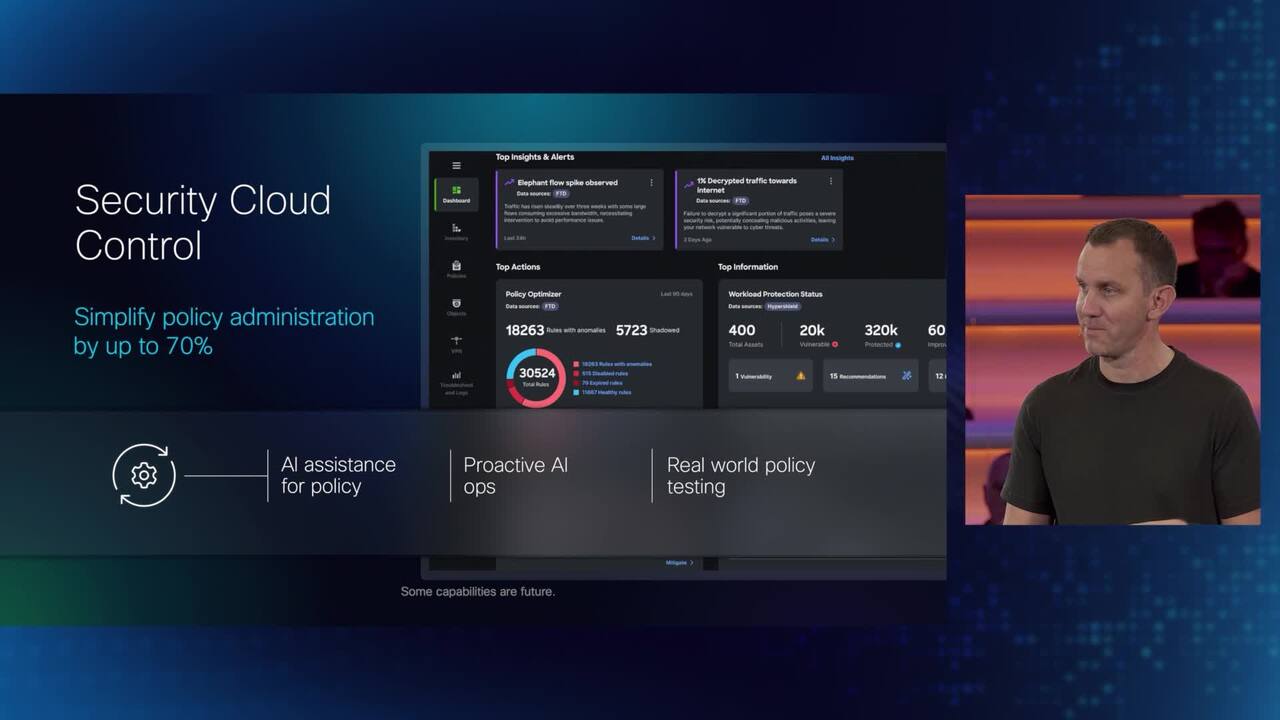
Play video Unified management with Security Cloud Control
Unified management with Security Cloud Control
Hear Cisco Security CTO, Craig Connors explain how Security Cloud Control delivers unified management for Hybrid Mesh Firewall
2:23
-
Play video Cisco N9300 Series Smart Switches with Cisco Hypershield
Cisco N9300 Series Smart Switches with Cisco Hypershield
Taking a revolutionary step forward in data center security with the Cisco N9300 Series Smart Switches. Powered by Cisco Hypershield, these new switches integrate networking and security into a single solution.
3:12
-
Play video Cisco Nexus Smart Switch and Hypershield Integration
Cisco Nexus Smart Switch and Hypershield Integration
In this session, our experts introduce a new family of Nexus data center Smart Switches with DPUs, enabling stateful services to be embedded directly into the data center fabric at scale.
1:02:40
-
Play video How United Airlines Secures Global Operations with Cisco Secure Workload | How I Cisco
How United Airlines Secures Global Operations with Cisco Secure Workload | How I Cisco
Shawn Walker of United Airlines shares how Cisco Secure Workload protects one of the largest airline networks. With 600+ locations and millions of customers, United boosts visibility, automates processes, and secures hybrid environments.
1:06
-
Play video Making your big security challenges manageable, with Cisco XDR and Meraki MX
Making your big security challenges manageable, with Cisco XDR and Meraki MX
The native integration of Meraki MX with Cisco XDR makes it easy to correlate netflow data with telemetry from email, endpoints, servers, and cloud workloads to deliver network-led insights in prioritizing developing threats across your environment.
1:11