Cisco Secure Firewall: Strength in Unity
1:40
There is strength in unity, and when it comes to protecting the integrity of your organization, the same holds true. You need multiple security tools working together to protect your network, workforce, and workloads.
Related Videos
In Security
-
Play video AI-Ready Wireless Security: Integrating WPA3 & Beyond
AI-Ready Wireless Security: Integrating WPA3 & Beyond
Delve into AI-Ready Wireless Security: WPA3's evolution from WEP, its role in Wi-Fi 6E/7 (MLO, EHT), and enhanced cryptography. Covers holistic network security & emerging post-quantum cryptography to counter future threats.
18:53
-
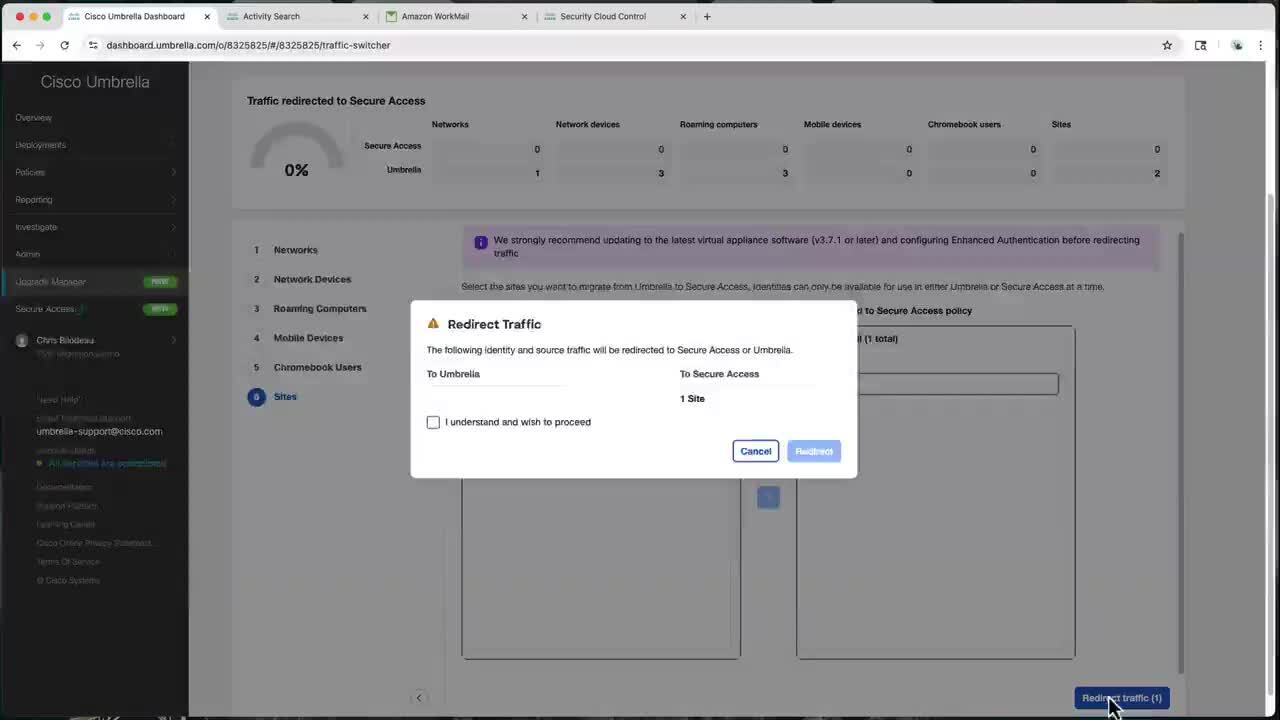
Play video Moving to Cisco Secure Access: Cisco Umbrella DNS Migration Tutorial
Moving to Cisco Secure Access: Cisco Umbrella DNS Migration Tutorial
Watch this brief video for a step-by-step guide for how to migrate from Cisco Umbrella DNS to Cisco Secure Access - DNS Defense using the automated upgrade manager.
12:22
-
Play video Cisco Cyber Vision: Protecting OT at Scale
Cisco Cyber Vision: Protecting OT at Scale
Get unparalleled visibility and threat detection across operational technology networks by analyzing industrial protocols and integrating with Cisco security products to secure OT environments at scale.
1:56
-
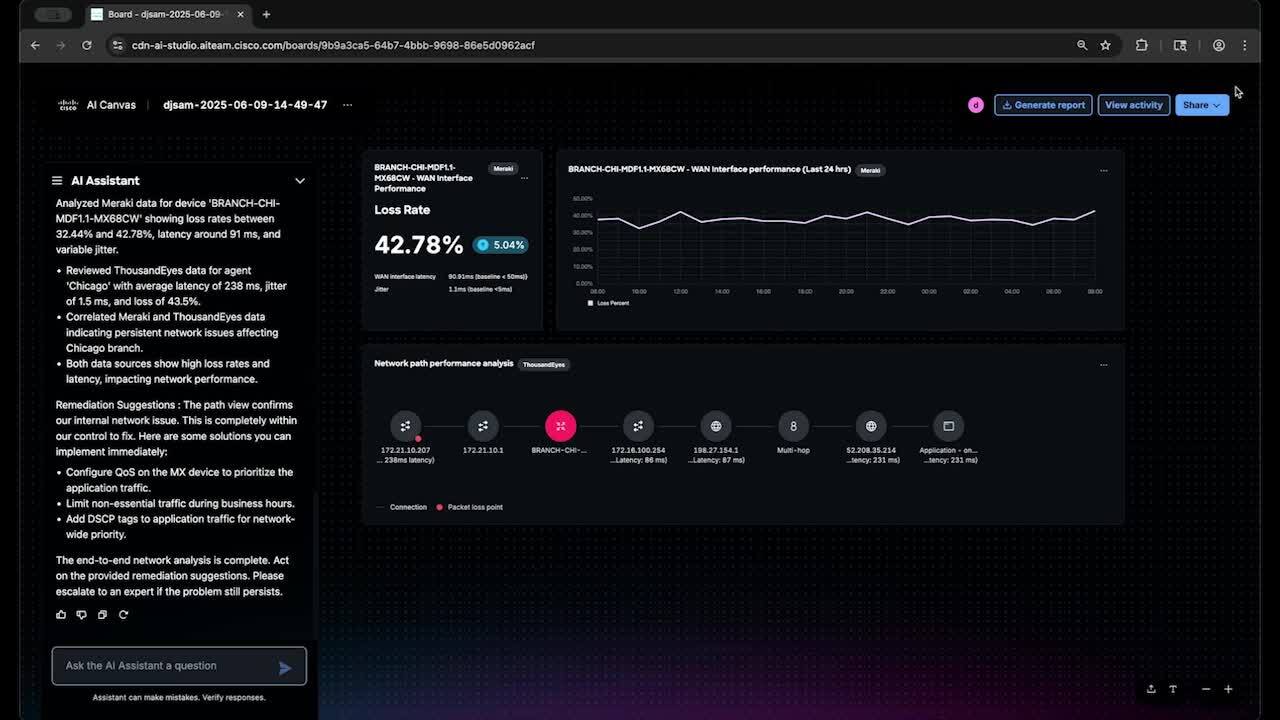
Play video Introducing Cisco AI Canvas — The AgenticOps Revolution
Introducing Cisco AI Canvas — The AgenticOps Revolution
AI Canvas is Cisco's first Generative UI for cross-domain IT-a shared, intelligent workspace that brings real-time telemetry, AI insights, and team collaboration into one view. Built for AgenticOps, it transforms how NetOps, SecOps, and app teams sol
6:26
-
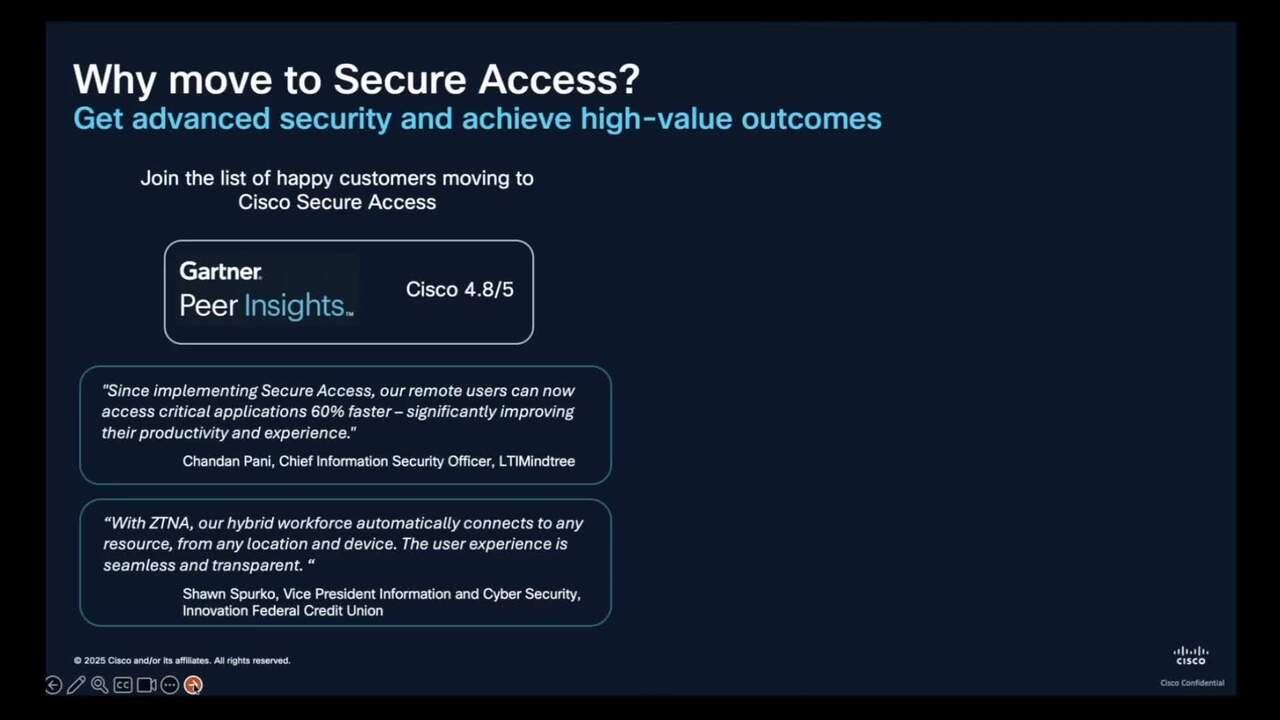
Play video Unlock Advanced Protection: Migrate from Cisco Umbrella to Cisco Secure Access
Unlock Advanced Protection: Migrate from Cisco Umbrella to Cisco Secure Access
Watch this video for a breakdown of the top 5 reasons why you should migrate to Secure Access.
14:26
-
Play video Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods partnered with Cisco to modernize security by replacing legacy systems with a secure access service edge (SASE) framework. The company's goals are to unify networking and security, enable zero trust and streamline management.
2:55