Advanced Attacker Automation: Botnet capabilities and techniques used to evade your defences
31:55
David Warburton (F5) - Presentation from SECCON NL 2022
Related Videos
In Security
-
Play video Cisco Cyber Vision: Protecting OT at Scale
Cisco Cyber Vision: Protecting OT at Scale
Get unparalleled visibility and threat detection across operational technology networks by analyzing industrial protocols and integrating with Cisco security products to secure OT environments at scale.
1:56
-
Play video Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods Goes Zero Trust: Modern Security with Cisco SASE
Peco Foods partnered with Cisco to modernize security by replacing legacy systems with a secure access service edge (SASE) framework. The company's goals are to unify networking and security, enable zero trust and streamline management.
2:55
-
Play video AI-Ready Wireless Security: Integrating WPA3 & Beyond
AI-Ready Wireless Security: Integrating WPA3 & Beyond
Delve into AI-Ready Wireless Security: WPA3's evolution from WEP, its role in Wi-Fi 6E/7 (MLO, EHT), and enhanced cryptography. Covers holistic network security & emerging post-quantum cryptography to counter future threats.
18:53
-
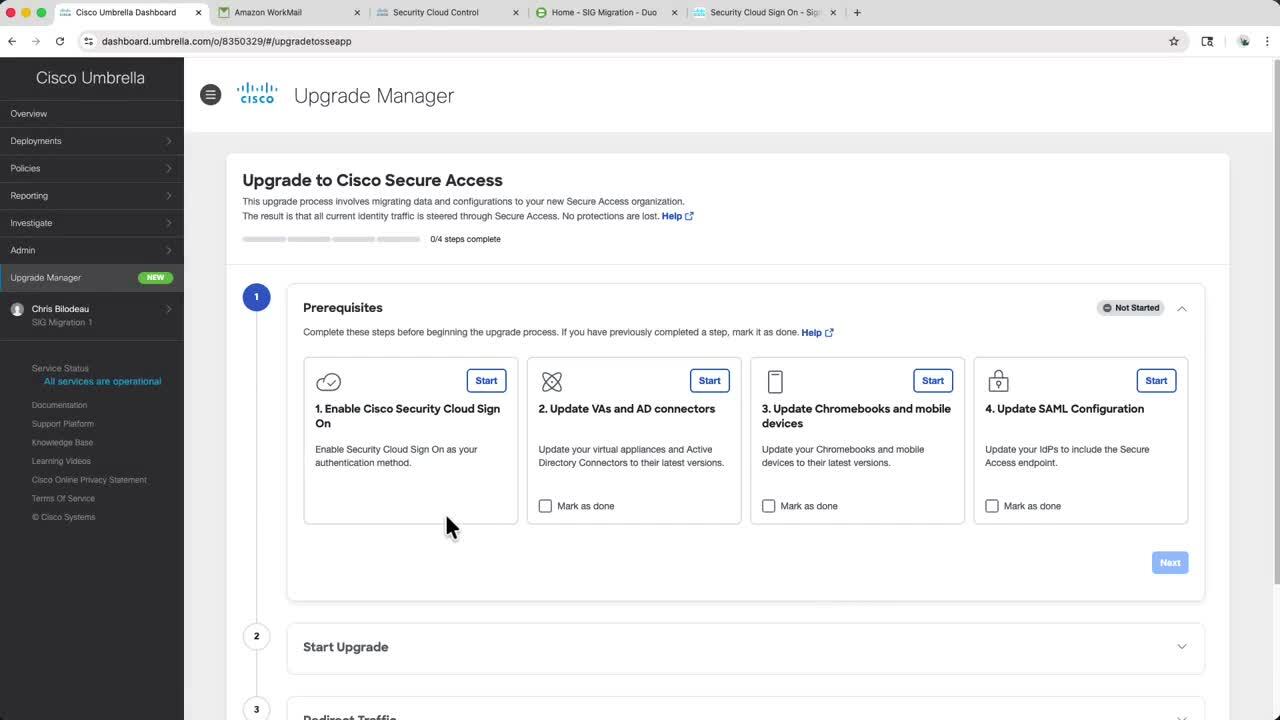
Play video Moving to Cisco Secure Access: Cisco Umbrella SIG Migration Tutorial
Moving to Cisco Secure Access: Cisco Umbrella SIG Migration Tutorial
Watch this video for a step-by-step guide of how to migrate from Cisco Umbrella SIG to Cisco Secure Access - Secure Internet Access (SIA) leveraging the automated upgrade manager.
8:28
-
Play video Birla Opus Paints - Connected Factories, Smarter Paint
Birla Opus Paints - Connected Factories, Smarter Paint
Birla Opus Paints built six new factories with one digital backbone, achieving speed, security, and resilience through Cisco-powered connected operations.
1:47
-
Play video The AI Ready Enterprise: Building a Secure Network Architecture for What's Next
The AI Ready Enterprise: Building a Secure Network Architecture for What's Next
Campus networks are under pressure— increased traffic, AI workloads, hybrid work, and a rising tide of IoT devices create unprecedented risks. Simplify and secure your AI-ready infrastructure with scalable, integrated security solutions to deliver a
2:22