Embedded cloud-native security with AWS
55:58
Check out our webinar to learn how AWS and Cisco are working together to help customers improve their cloud security.
Related Videos
In Network Protection
-
Play video Secure remote access with Cisco Identity Services Engine
Secure remote access with Cisco Identity Services Engine
Remote work is projected to jump up 83% in frequency, it’s not going anywhere. Extend the zero-trust workplace to anywhere and on anything with unified policy and control from ISE.
2:00
-
Play video Cisco Secure Cloud Analytics Demo
Cisco Secure Cloud Analytics Demo
Watch our on-demand video demo and see how you can achieve a comprehensive approach to gaining visibility and telemetry for actionable analytics across your hybrid infrastructure to detect threats.
7:31
-
Play video Cisco Stealthwatch for Multicloud Security
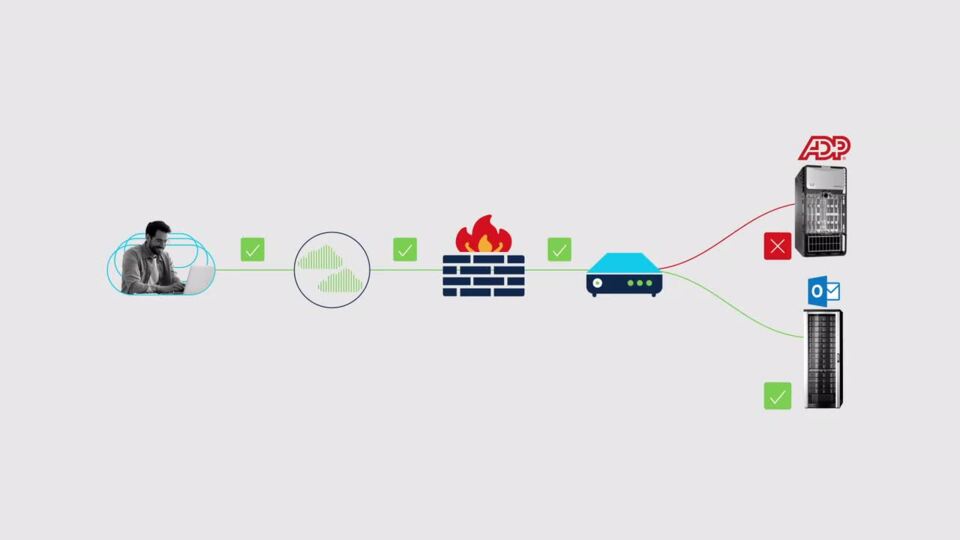
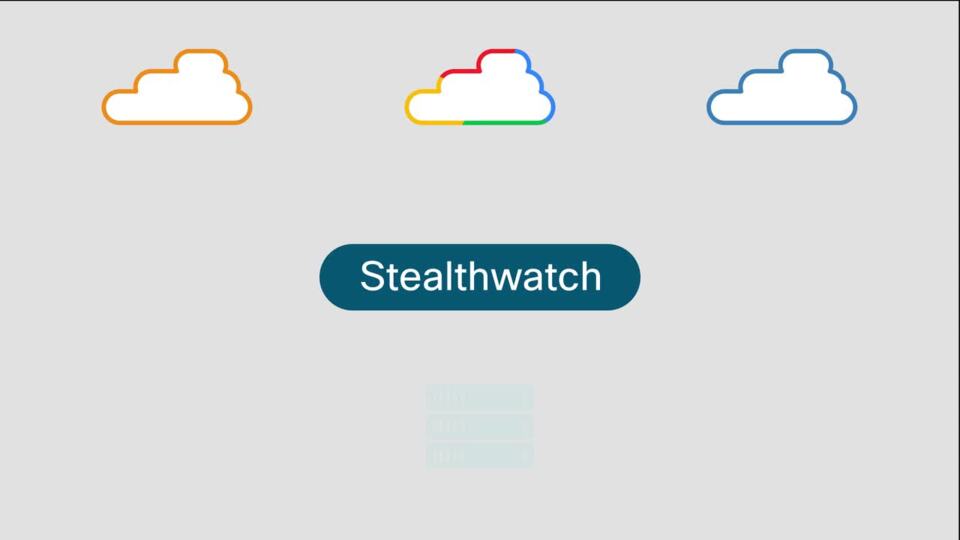
Cisco Stealthwatch for Multicloud Security
Cisco Stealthwatch can ingest native logs from AWS, Google Cloud Platform, Microsoft Azure, and the on-premises network. This gives you a unified view of your entire network to detect and investigate threats wherever they are.
1:39
-
Play video Cisco Secure Cloud Analytics Overview
Cisco Secure Cloud Analytics Overview
See how you can achieve a comprehensive approach to gaining visibility and telemetry for actionable analytics across your hybrid infrastructure to detect threats.
2:15
-
Play video Cisco Stealthwatch Cloud in 2 minutes
Cisco Stealthwatch Cloud in 2 minutes
Learn how Cisco Stealthwatch Cloud can help you secure your public cloud, private network, or hybrid environment.
1:39
-
Play video Centralized log management with Security Analytics and Logging
Centralized log management with Security Analytics and Logging
Learn how to aggregate and analyze logs at scale with Security Analytics and Logging. To learn more please visit https://www.cisco.com/go/security-analytics-logging
1:45