How can I generate a license authorization code, in Cisco License Central (CLC)?
3:13
Generate a license authorization code, in Cisco License Central (CLC)
Related Videos
In Latest Videos
-
Play video Cisco N9000: 51.2T Switching Built for Distributed AI Workloads
Cisco N9000: 51.2T Switching Built for Distributed AI Workloads
Distributed AI workloads demand next-generation infrastructure. Cisco N9000 switches powered by Cisco Silicon One P200 deliver 51.2T capacity, high-density 800G performance, and security on every port—all unified under Cisco Nexus One.
2:00
-
Play video Cisco Silicon One G300: Intelligent AI Networking at 102.4 Terabits per Second
Cisco Silicon One G300: Intelligent AI Networking at 102.4 Terabits per Second
Meet Cisco Silicon One G300—purpose-built for demanding AI workloads with 102.4 Tbps connectivity. Features industry-leading shared buffer, fabric-aware load balancing and programmable architecture.
1:48
-
Play video The Future of AI Networking: Intelligence, Performance, and Security
The Future of AI Networking: Intelligence, Performance, and Security
Transform fragmented data centers into unified AI infrastructure. Cisco Nexus One offers breakthrough performance for massive clusters, intelligent packet flow, agentic operations, and security woven into the fabric. When networks match AI ambitions.
2:21
-
Play video Smart Licensing using VRF Configuration in IOS XR
Smart Licensing using VRF Configuration in IOS XR
This video demonstrates configuration steps for smart licensing when a communication occurs within a vrf on Cisco XR platforms. Tags: smart, IOSXR
3:03
-
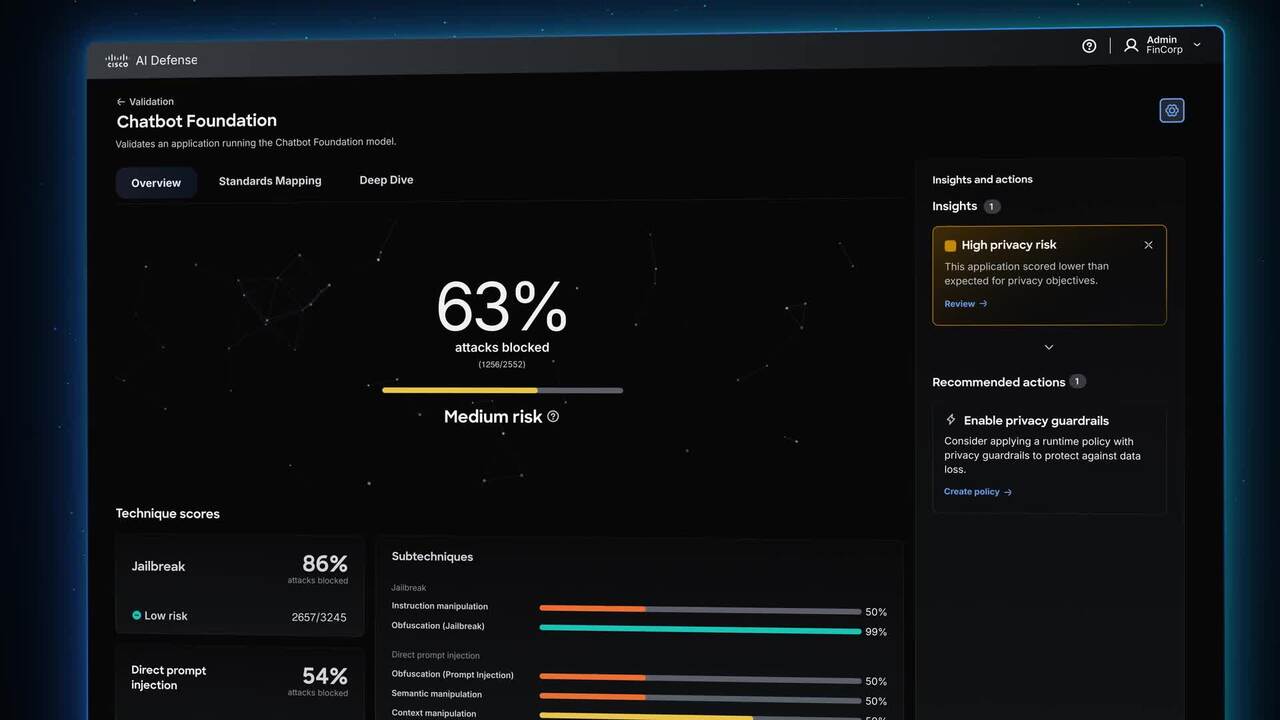
Play video Meet Cisco AI Defense
Meet Cisco AI Defense
Security built for the AI era. What stands between you and AI's promise is the unknown-new attack vectors, hidden AI assets, and risks traditional security can't see. Cisco AI Defense secures the AI lifecycle so teams can innovate with confidence.
2:19
-
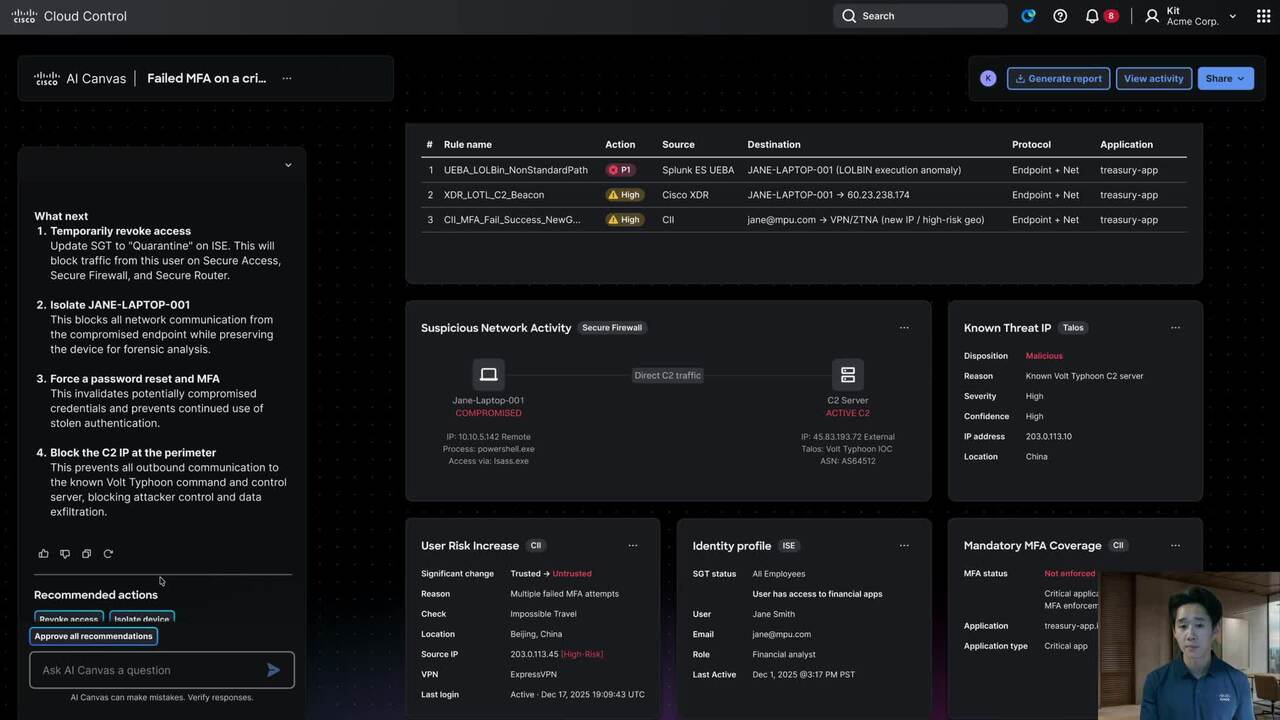
Play video AI Canvas troubleshoots across security and networking domains
AI Canvas troubleshoots across security and networking domains
AI Canvas correlates identity, endpoint, and network signals to detect a Volt Typhoon-style compromise, contain the breach, harden access with MFA and ZTNA, and protect critical financial apps with segmentation and continuous monitoring.
4:10