Local Upgrade of the Cisco Security Manager Demonstration
1:59
This video demonstrates general steps for local upgrade of the CSM Tags: asa,security
Related Videos
In Latest Videos
-
Play video How to Move Tech-Support Files from Admin VM to XR VM
How to Move Tech-Support Files from Admin VM to XR VM
This video demonstrates how to collect the admin show tech files from Advim VM. Tags: ios-xr, showtech
3:15
-
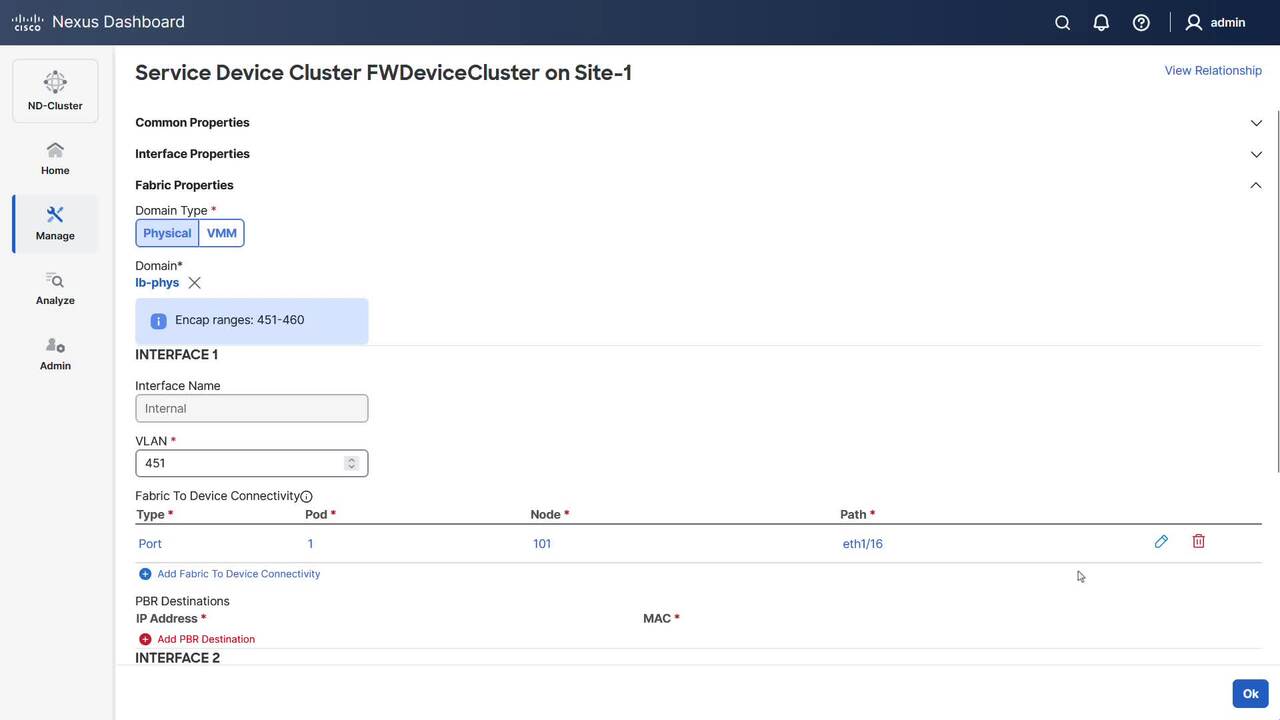
Play video Configure Service Chaining for E-W Traffic in NDO
Configure Service Chaining for E-W Traffic in NDO
This video demonstrates how to configure service chaining in NDO for EPG-to-EPG communication in single site.
6:25
-
Play video Desk Pro G2 Demo
Desk Pro G2 Demo
Desk Pro G2 Demo
1:58
-
Play video Cisco Live EMEA 2026: The Factory of the Future - Hockey Puck Production
Cisco Live EMEA 2026: The Factory of the Future - Hockey Puck Production
From the first drop to the final goal, our hockey puck demo at Cisco Live EMEA highlighted how manufacturers score with AI machine vision and virtualization - all powered by Cisco's reliable, secure industrial networking.
5:46
-
Play video Cisco at the S4x26 POC Pavilion
Cisco at the S4x26 POC Pavilion
At the S4x26 conference, Cisco was part of the POC Pavilion where Dale Peterson challenged vendors to demonstrate real-world industrial security—live! Cisco's visibility driven network segmentation and OT SOC workflows were highly regarded.
11:20
-
Play video Cisco Live EMEA 2026: 20/20 Vision into OT Cyber Risks with ZEISS
Cisco Live EMEA 2026: 20/20 Vision into OT Cyber Risks with ZEISS
In factories and roadways, cybersecurity is vital for safety and resilience. Hear from Thrasyvoulos Mystiroudis, Senior Manager, Network and Connectivity at ZEISS on how they're securing production with full visibility into industrial assets.
5:23