Protect identities
0:31
Discover accounts that may be at risk, or pose a risk. Use phishing-resistant multi-factor authentication (MFA) on all apps—legacy and modern ones—in a way that frustrates attackers and not users.
Related Videos
In Latest Videos
-
Play video Cisco Tech Bytes: Universal ZTNA
Cisco Tech Bytes: Universal ZTNA
Is the idea of perimeter security obsolete? Hear Eric Knipp and Jamey Heary discuss Universal Zero Trust Network Access (ZTNA) and how Cisco is helping customers secure their network and application access differently.
11:30
-
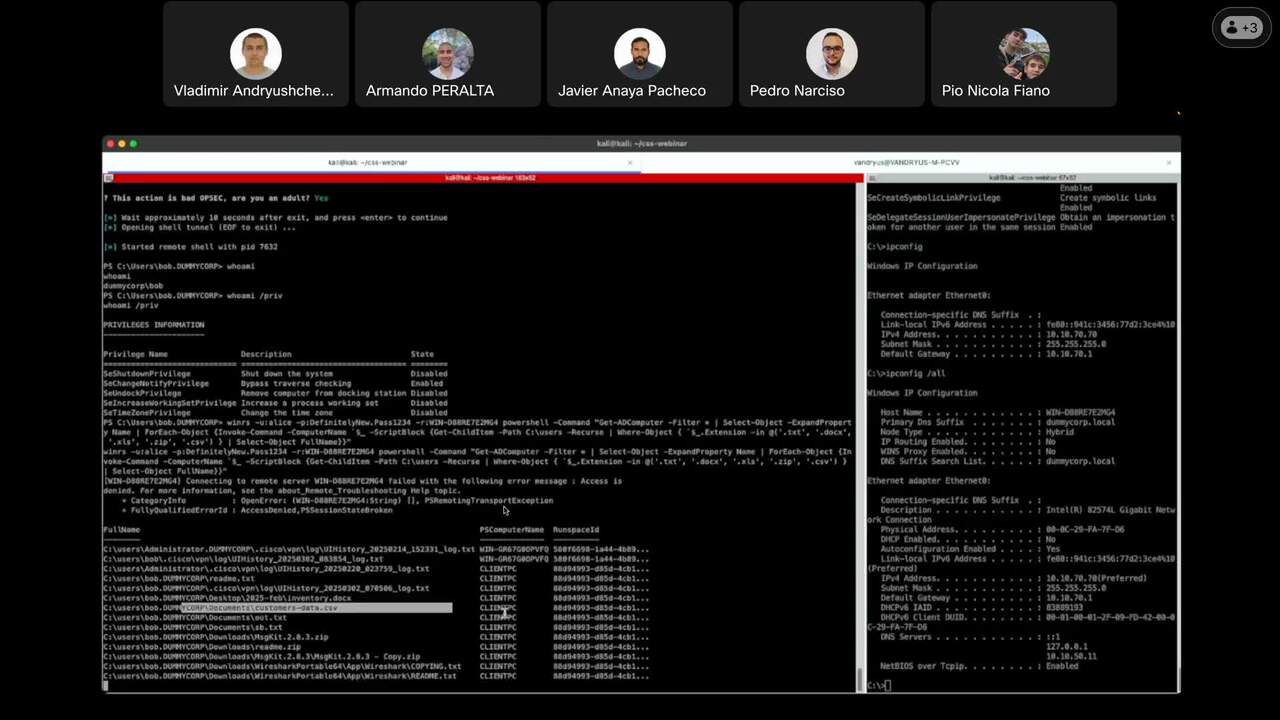
Play video Cybersecurity Threats Exposed: Real-World Attacks and Cisco Defenses
Cybersecurity Threats Exposed: Real-World Attacks and Cisco Defenses
Showcase of progression from an initial breach to full exploitation. Using real-world scenarios, illustration of the methods attackers use to infiltrate systems, exfiltrate data, and disrupt operations.
1:28:18
-
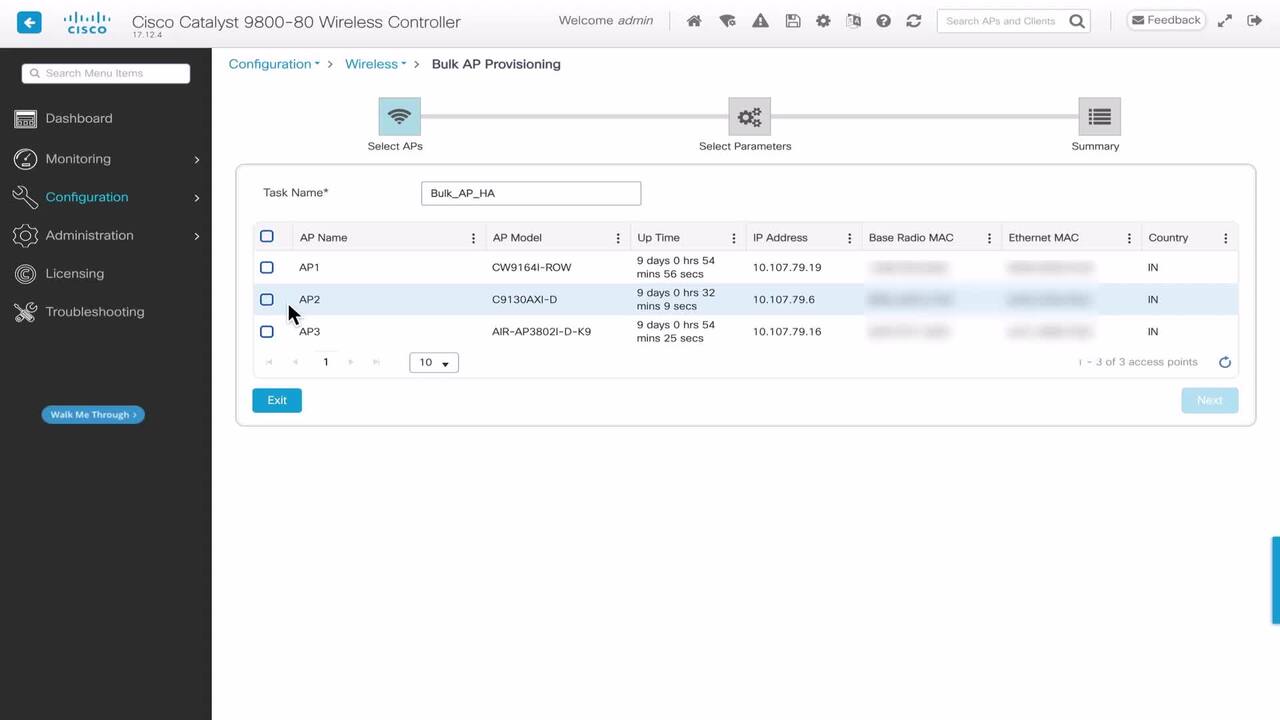
Play video Use Bulk AP Provisioning for High-Availability Configuration
Use Bulk AP Provisioning for High-Availability Configuration
This video demonstrates a configuration setup for Bulk AP Provisioning of High Availability Configuration on the C9800. Tags: Wireless, C9800
2:41
-
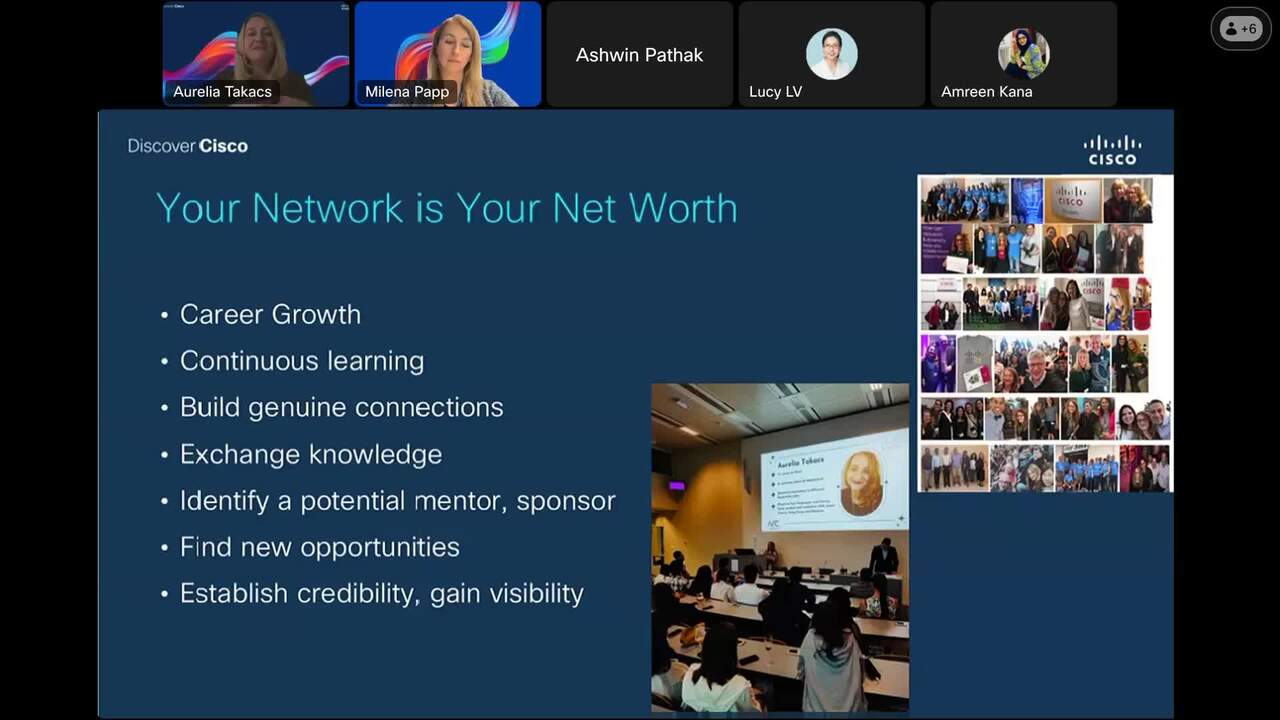
Play video Discover Cisco at a Glance: Building Your Professional Network
Discover Cisco at a Glance: Building Your Professional Network
Elevate your professional journey with the power of networking! Start building meaningful and long-lasting industry relationships by leveraging social media platforms, and identify potential mentors or sponsors.
57:24
-
Play video Making your big security challenges manageable, with Cisco XDR and Meraki MX
Making your big security challenges manageable, with Cisco XDR and Meraki MX
The native integration of Meraki MX with Cisco XDR makes it easy to correlate netflow data with telemetry from email, endpoints, servers, and cloud workloads to deliver network-led insights in prioritizing developing threats across your environment.
1:11
-
Play video DC Segmentation with VXLAN Group Policy Object (GPO) On-Demand Webinar
DC Segmentation with VXLAN Group Policy Object (GPO) On-Demand Webinar
Join this webinar to discover how you can implement segmentation on VXLAN EVPN fabrics with Nexus and the Group Policy Object (GPO) capabilities. Live demo included
1:34:26