How to Collect Tech-Support Logs on NCS2K
1:35
This video explains how to use the Tech-Support script; a command line utility that is used to collect diagnostic logs from NCS2k Tags: ncs2k,logcollection
Related Videos
In Latest Videos
-
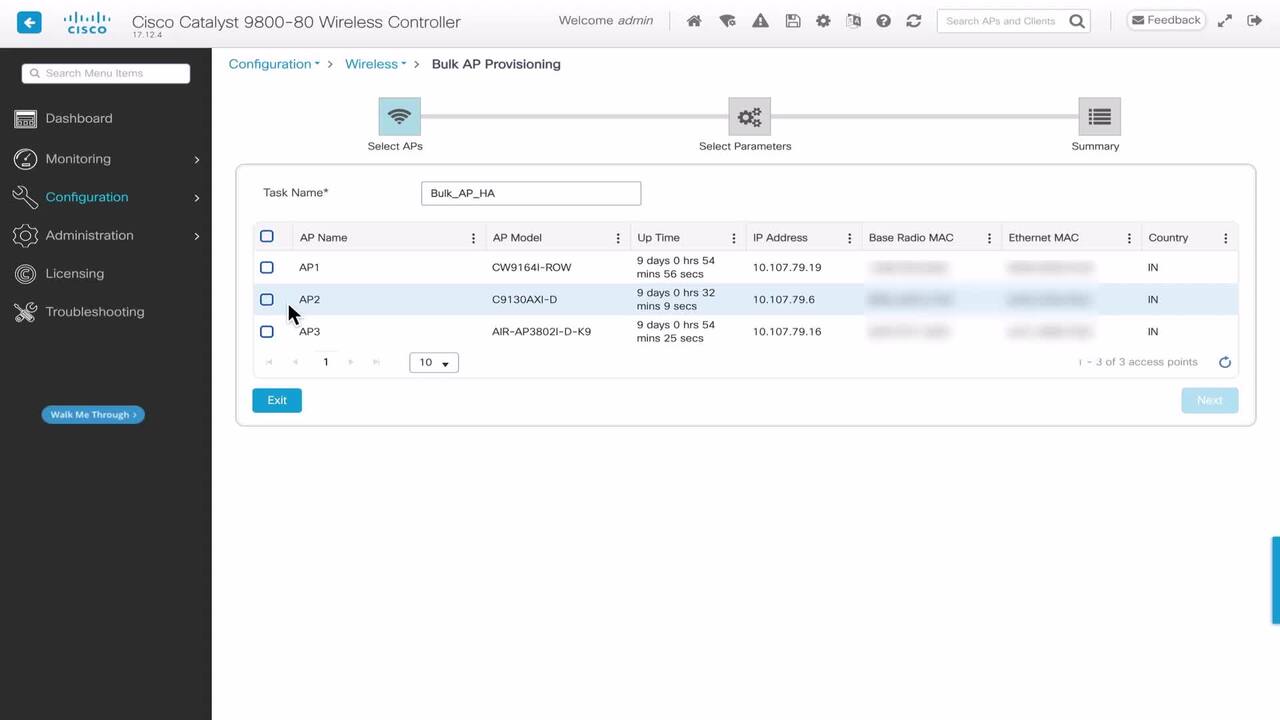
Play video Use Bulk AP Provisioning for High-Availability Configuration
Use Bulk AP Provisioning for High-Availability Configuration
This video demonstrates a configuration setup for Bulk AP Provisioning of High Availability Configuration on the C9800. Tags: Wireless, C9800
2:41
-
Play video DC Segmentation with VXLAN Group Policy Object (GPO) On-Demand Webinar
DC Segmentation with VXLAN Group Policy Object (GPO) On-Demand Webinar
Join this webinar to discover how you can implement segmentation on VXLAN EVPN fabrics with Nexus and the Group Policy Object (GPO) capabilities. Live demo included
1:34:26
-
Play video Cisco Tech Bytes: Universal ZTNA
Cisco Tech Bytes: Universal ZTNA
Is the idea of perimeter security obsolete? Hear Eric Knipp and Jamey Heary discuss Universal Zero Trust Network Access (ZTNA) and how Cisco is helping customers secure their network and application access differently.
11:30
-
Play video SheSpeaks+ Embracing a Lifelong Learning Mindset
SheSpeaks+ Embracing a Lifelong Learning Mindset
Join Marci Paino, VP of Enterprise Learning & Growth and Chief Learning Officer, for an engaging session on leadership development, career progression, and impactful experiential learning.
58:34
-
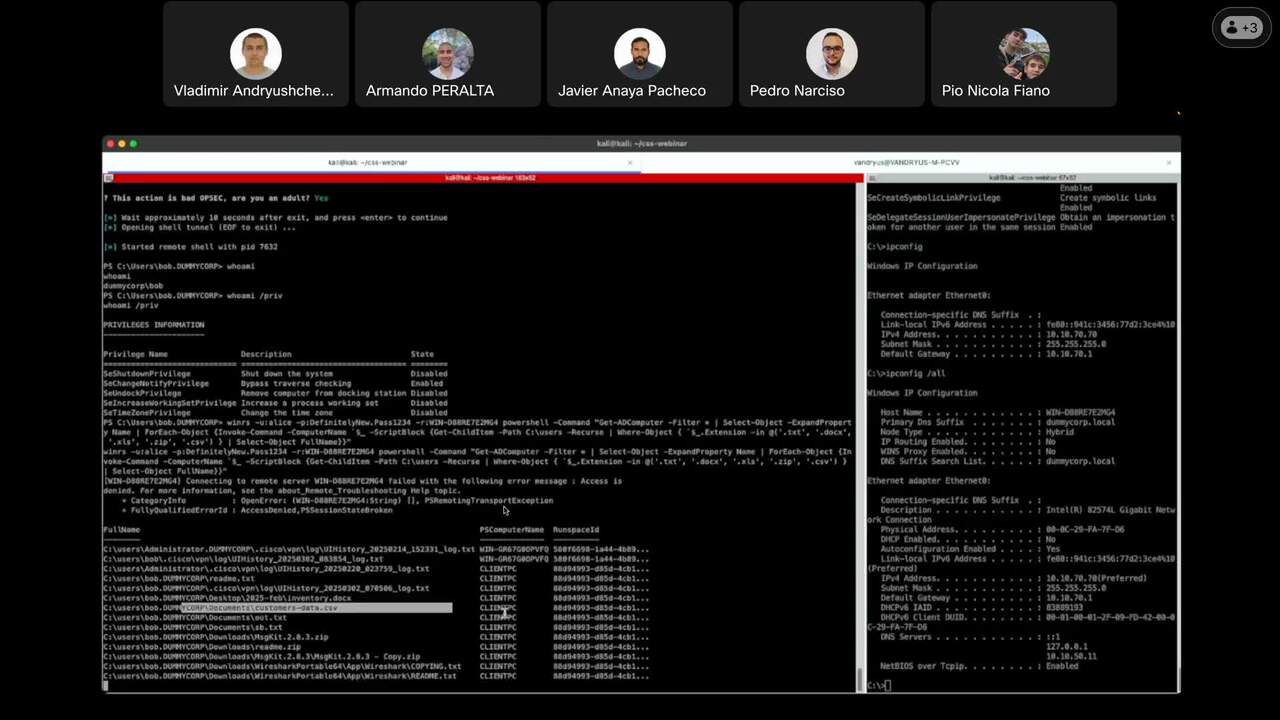
Play video Cybersecurity Threats Exposed: Real-World Attacks and Cisco Defenses
Cybersecurity Threats Exposed: Real-World Attacks and Cisco Defenses
Showcase of progression from an initial breach to full exploitation. Using real-world scenarios, illustration of the methods attackers use to infiltrate systems, exfiltrate data, and disrupt operations.
1:28:18
-
Play video Making your big security challenges manageable, with Cisco XDR and Meraki MX
Making your big security challenges manageable, with Cisco XDR and Meraki MX
The native integration of Meraki MX with Cisco XDR makes it easy to correlate netflow data with telemetry from email, endpoints, servers, and cloud workloads to deliver network-led insights in prioritizing developing threats across your environment.
1:11