Explore Advanced ACI Use Cases with Layer-3 Mode
55:28
Learn how to transit from Layer 2 to Layer 3 and how this transition can significantly improve your data center operations with enhanced scalability, simplified network management, and improved security.
Related Videos
In Latest Videos
-
Play video Catalyst IW9165E: a rugged, compact and ultra-reliable access point
Catalyst IW9165E: a rugged, compact and ultra-reliable access point
Meet the Catalyst IW9165E: engineered for ultra-reliable connectivity in your most dynamic environments. This rugged, compact access point and wireless client integrates Wi-Fi with URWB, ensuring seamless handoffs and near-zero latency.
3:38
-
Play video Demo: Transform Service Delivery with Cisco Routed PON
Demo: Transform Service Delivery with Cisco Routed PON
Discover how Cisco Routed PON empowers service providers to deliver bandwidth cost effectively and at scale with a resilient, secure network that collapses IP and optical into a single layer. Watch this demo for an in-depth look at how it works.
14:03
-
Play video Digitally empowering the Amazon's remote communities
Digitally empowering the Amazon's remote communities
Born in a remote fishing village in the Amazon, Joao was searching for more opportunities for his education. With the help of the Cisco Networking Academy, he is setting his sights on new goals and bringing digital skills to his home town.
6:45
-
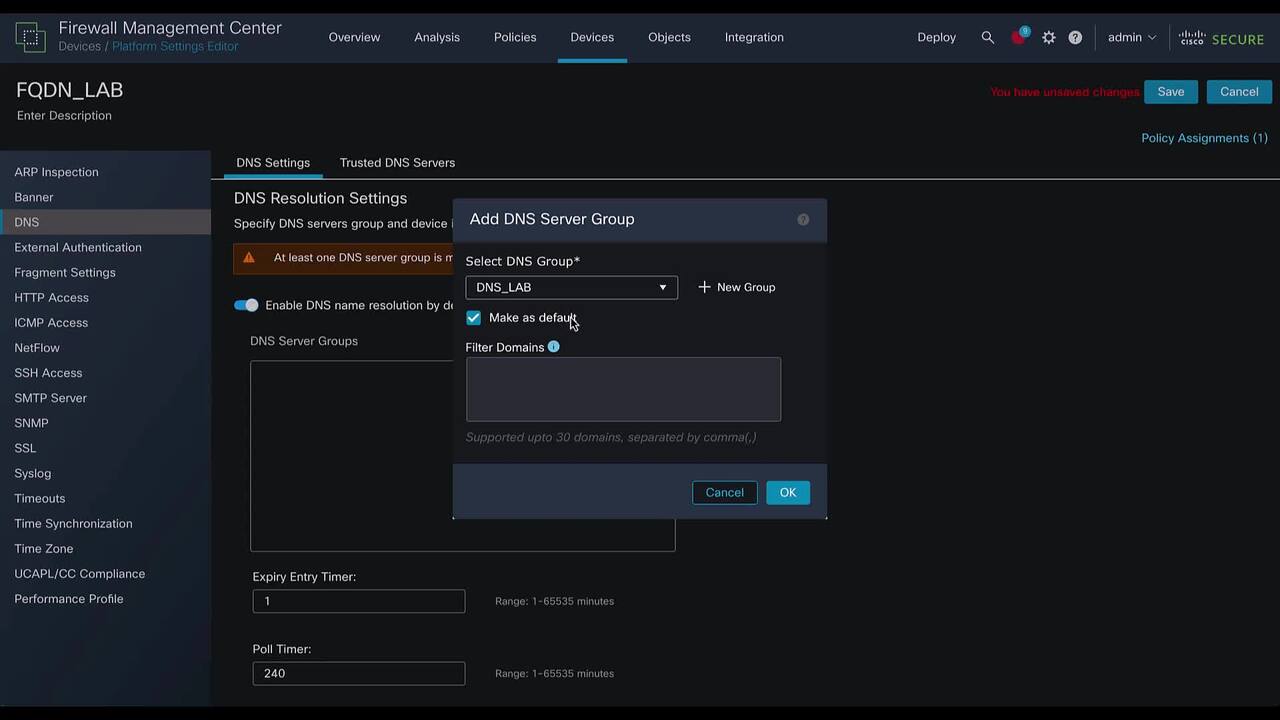
Play video Use of FQDN Object in Access Policy Firepower Threat Defense
Use of FQDN Object in Access Policy Firepower Threat Defense
This video demonstrates the use of FQDN object in access policy on Firepower Threat Defense Tags: Security Firepower
3:27
-
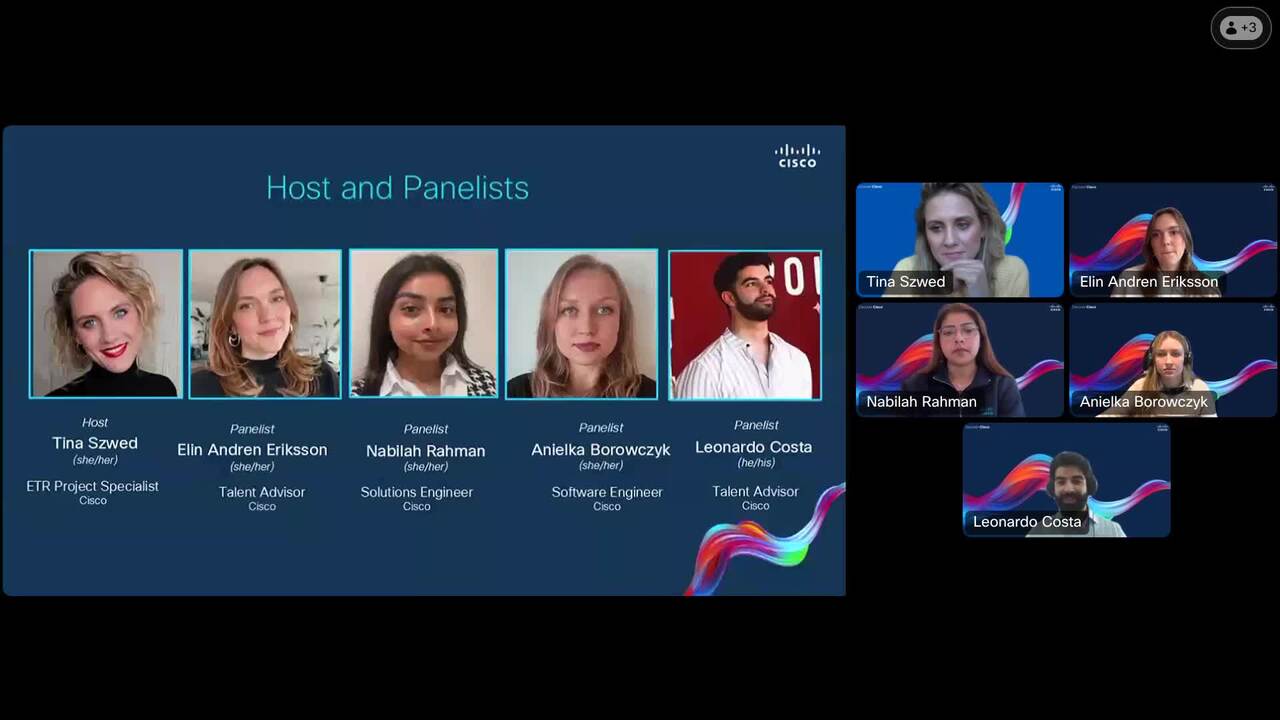
Play video Discover Cisco at a Glance: How to Get Hired
Discover Cisco at a Glance: How to Get Hired
A live Q&A session that designed to give students and early-career talent direct access to recruiters and recent graduates, and answer the questions about recruiting & Early In Career experience at Cisco.
55:57
-
Play video Automated Parking Revolution: HL Robotics Parkie Powered by Cisco URWB Technology
Automated Parking Revolution: HL Robotics Parkie Powered by Cisco URWB Technology
See how HL Robotics’ Parkie, powered by Cisco’s URWB, delivers seamless, automated parking. Discover the future of stress-free, connected parking and how advanced wireless tech makes it possible!
3:26