Use of FQDN Object in Access Policy Firepower Threat Defense
3:27
This is the demonstration on how to use FQDN object in firepower threat defense.
Related Videos
In Government
-
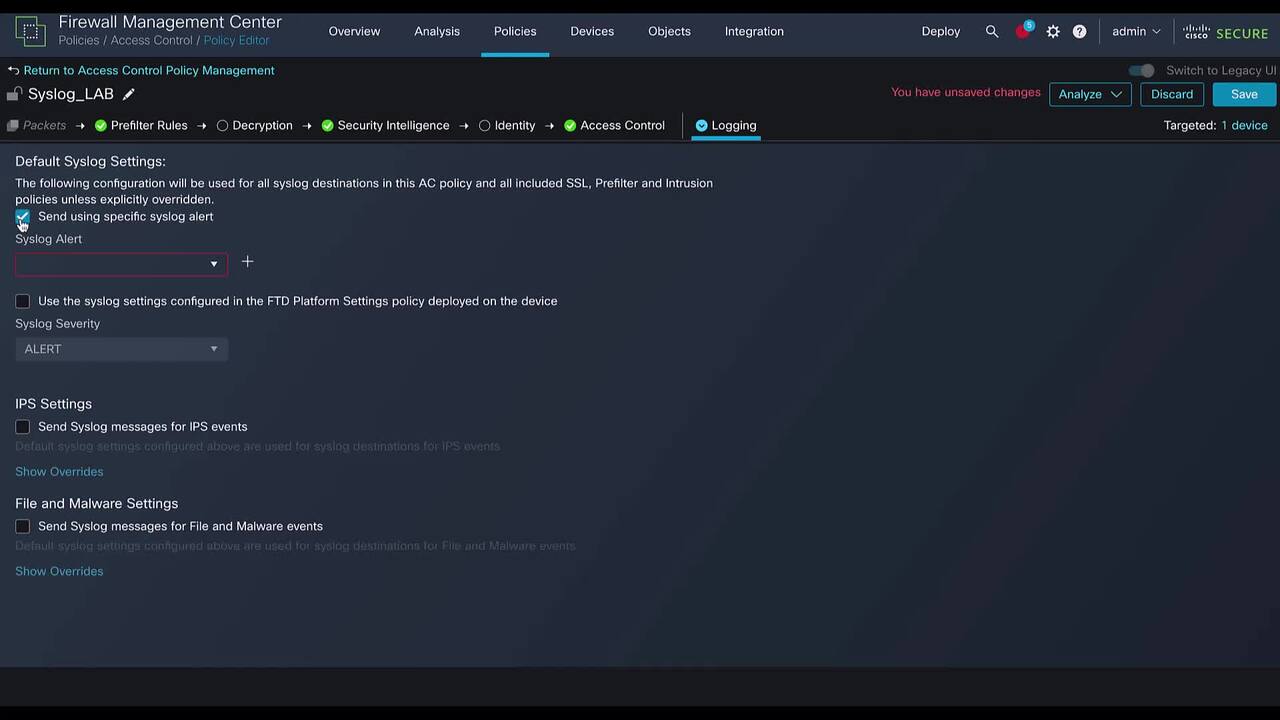
Play video Use alert action to send events to syslog server from FTD
Use alert action to send events to syslog server from FTD
This video demonstrate how to use alert action to send events to syslog server
2:58
-
Play video Tech Unscripted: Future-Proofed Workplaces
Tech Unscripted: Future-Proofed Workplaces
Tech Unscripted: IT leaders from NKYU, Innovation FCU & Winslow TG discuss future-proof workplaces. Learn ZTNA, Cisco Secure Access, high-density Wi-Fi, Smart Buildings & IT-security collaboration for seamless, secure, adaptable IT. Must-watch!
42:19
-
Play video UCS C880A M8
UCS C880A M8
Latest Cisco HGX B300 Server for high density AI Deployment
1:25
-
Play video The AI Ready Enterprise: Building a Secure Network Architecture for What's Next
The AI Ready Enterprise: Building a Secure Network Architecture for What's Next
Campus networks are under pressure— increased traffic, AI workloads, hybrid work, and a rising tide of IoT devices create unprecedented risks. Simplify and secure your AI-ready infrastructure with scalable, integrated security solutions to deliver a
2:22
-
Play video Enable AI Assistant on Secure Firewall Management Center
Enable AI Assistant on Secure Firewall Management Center
This video shows the steps to enable the AI assistant in Secure FMC Tags:AI,CiscoCloud
2:20
-
Play video Run Software Diagnostics Tool in Intersight Managed Mode
Run Software Diagnostics Tool in Intersight Managed Mode
This video demonstrates how to run the software diagnostics tool to test server components health. Tags: IMM, SDT
4:25