Dynamic split Tunneling Configuration On Cisco FTD managed by FMC
3:19
Configuration of Dynamic split tunneling on Cisco FTD managed by FMC .
Related Videos
In Featured Video
-
Play video Unified Branch Overview Video
Unified Branch Overview Video
As enterprises embed AI into everyday workflows, campus networks must evolve-simpler to operate, secure by design, and built for real-time performance. Cisco Secure Campus delivers this through Agentic Operations, security fused into the network, and
2:16
-
Play video Footholds in Infrastructure: Defending Service Providers from Cyberthreats
Footholds in Infrastructure: Defending Service Providers from Cyberthreats
Discover the key cyberthreats targeting service providers, from espionage-driven advanced persistent threats (APTs) to silent intrusions and tough infrastructure decisions, and the risks they pose to critical networks.
2:36
-
Play video Accelerate intelligent retail with AI-ready infrastructure
Accelerate intelligent retail with AI-ready infrastructure
AI is reshaping retail, from engagement to supply chain. Discover the essential AI infrastructure that powers real-time analytics, automation, and innovation for efficient, unified customer experiences.
3:20
-
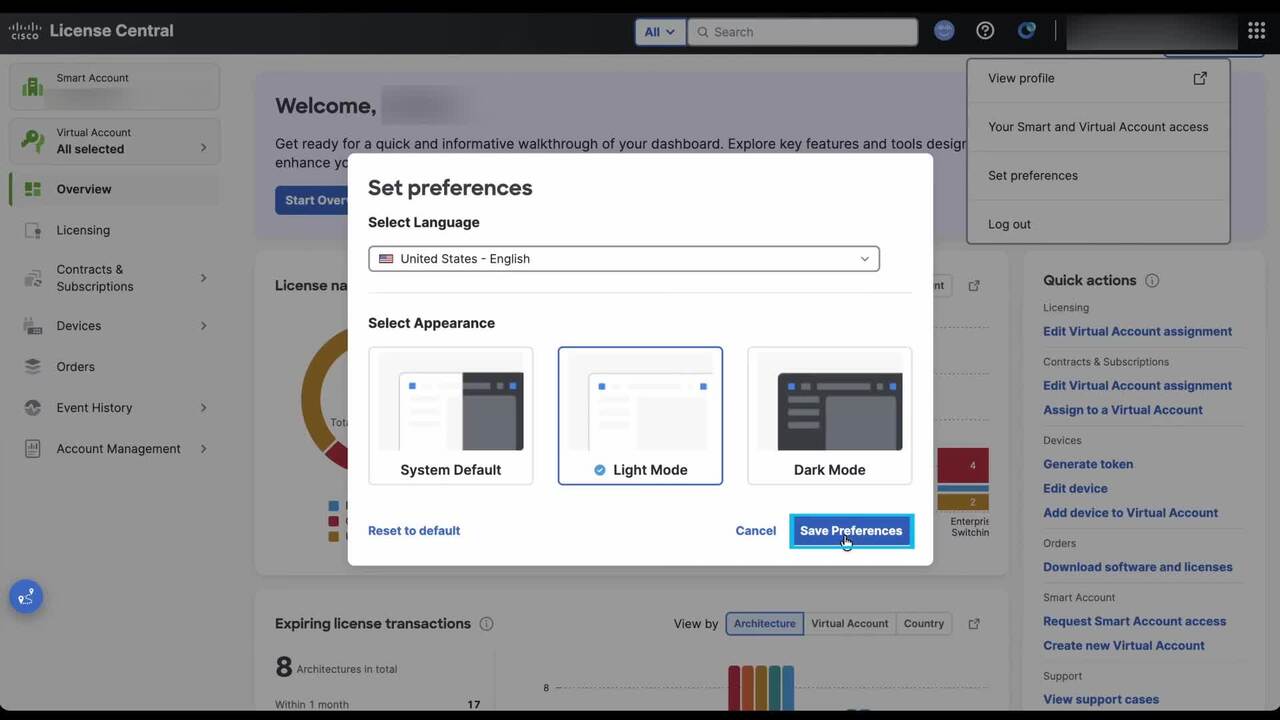
Play video How can I view the Overview page and Dashboard features , in License Central (LC)?
How can I view the Overview page and Dashboard features , in License Central (LC)?
View the Overview page and Dashboard features , in License Central
1:58
-
Play video Discover Cisco at a Glance: How to Get Hired
Discover Cisco at a Glance: How to Get Hired
A live Q&A session that designed to give students and early-career talent direct access to recruiters and recent graduates, and answer the questions about recruiting & Early In Career experience at Cisco.
55:57
-
Play video Cisco, E80, Planet Farms: Powering Industrial AI & Automation with Networks
Cisco, E80, Planet Farms: Powering Industrial AI & Automation with Networks
Andrea Orioli (Cisco), Massimo Mistretta (Planet Farms), and Fabio Oleari (E80) discuss how cutting-edge network infrastructure from Cisco enables AI-driven industrial automation, from AGVs to vertical farming. Originally posted by Industria Italiana
25:56