The Value of Telemetry – NX Foundations
42:13
Explore the advantages of enabling Catalyst Center telemetry and learn how to activate it step by step.
Related Videos
In Expert Insight Series
-
Play video End-to-end network management with Catalyst Center
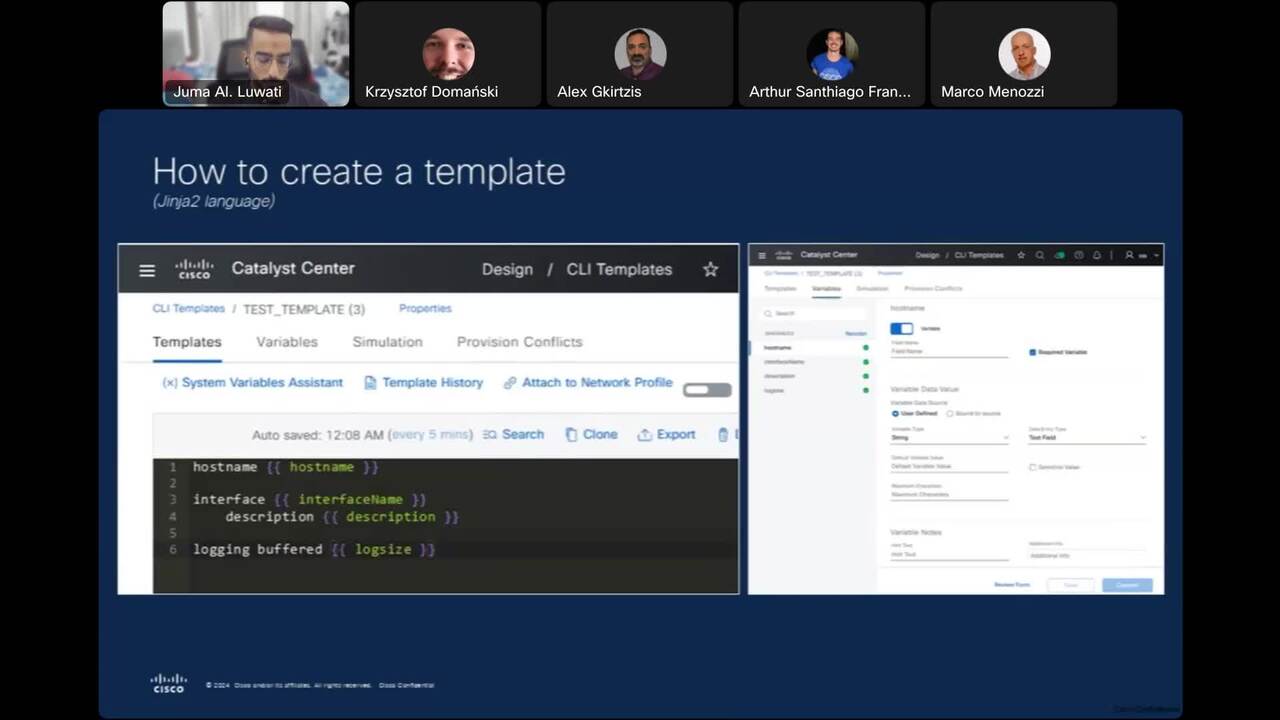
End-to-end network management with Catalyst Center
Leverage Catalyst Center to maintain a consistent and secure infrastructure by easily spotting network devices that don’t meet your standards. Harness the right resources to effectively remediate any compliance violations.
1:38:37
-
Play video What’s New in Catalyst Center 2.3.7
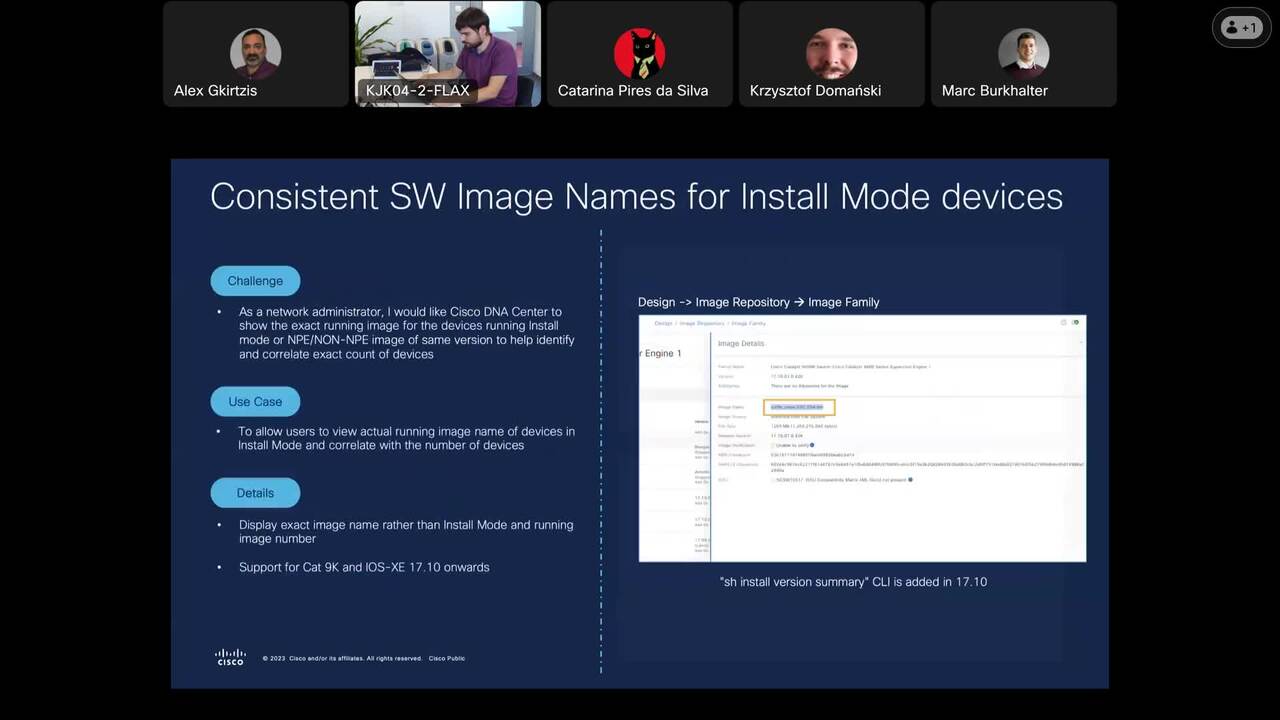
What’s New in Catalyst Center 2.3.7
Learn more about the latest Catalyst Center version and stay ahead of the IT curve with new assurance and automation features, as well as best practices to perform a smooth upgrade.
1:05:58
-
Play video Module 1 - Network Security Expert Series - Cisco Secure Firewall - English
Module 1 - Network Security Expert Series - Cisco Secure Firewall - English
Network security is vital for defending against cyberattacks, ensuring business continuity, and protecting both personal and organizational data from malicious activities.
3:22:51
-
Play video ACI 6.x Key Features & Upgrade Best Practices
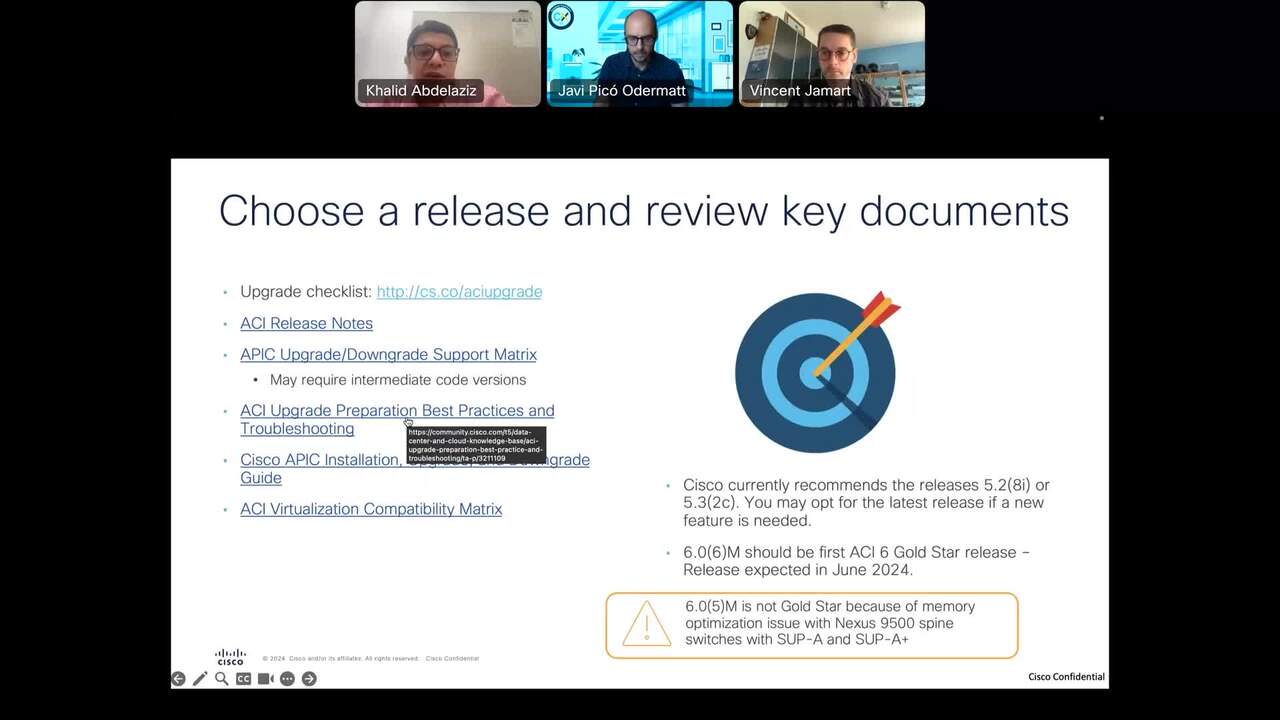
ACI 6.x Key Features & Upgrade Best Practices
Explore ACI 6.x new features & gain insights on best practices for a seamless upgrade. Discover how to increase visibility, enhance performance & simplify network management.
1:18:20
-
Play video Real Impact, Real Stories: Demonstrating Business Value with the Catalyst Center
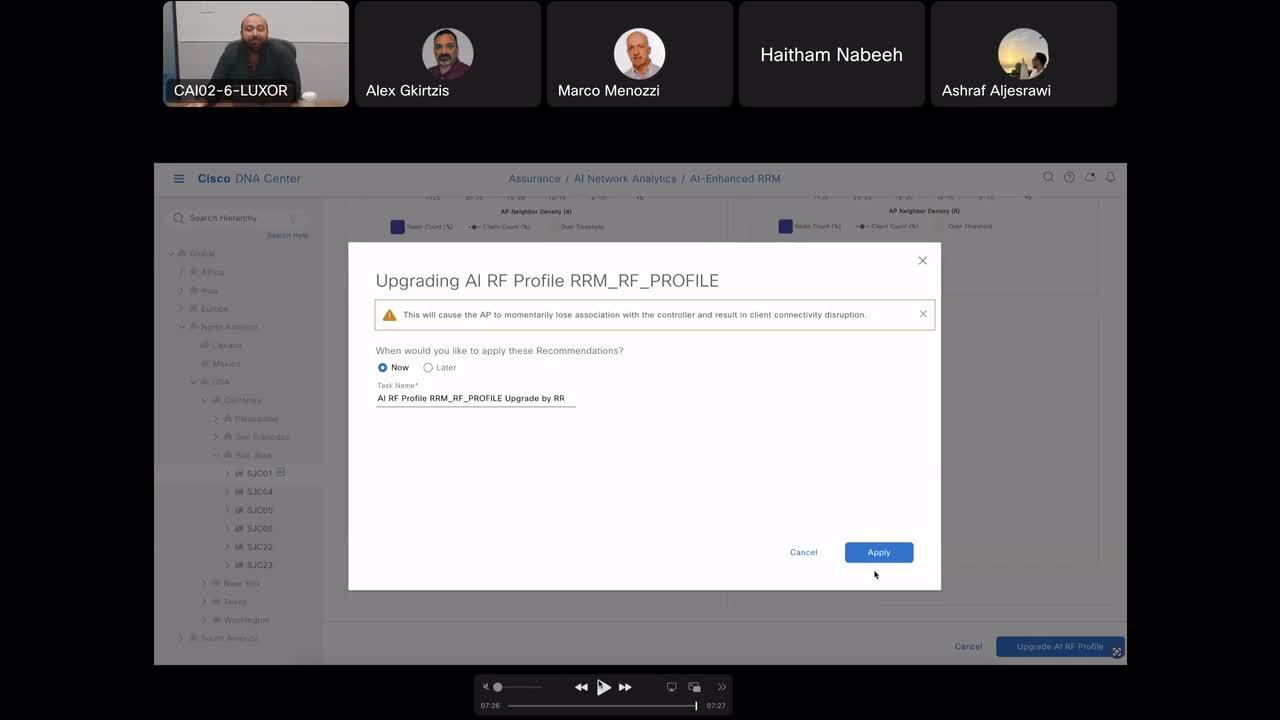
Real Impact, Real Stories: Demonstrating Business Value with the Catalyst Center
Discover business value of catalyst center, demonstrating real customer stories and showcasing variety of use cases that fulfils ever-increasing IT demands.
1:51:15
-
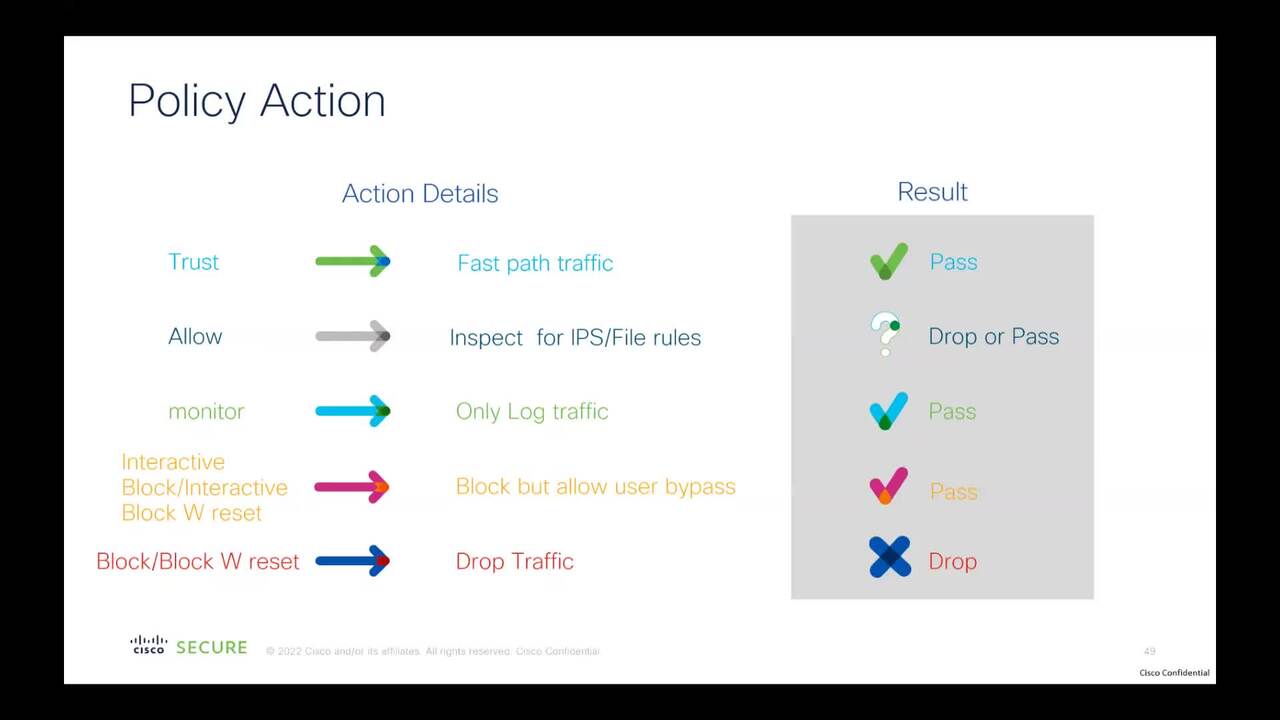
Play video Module 2 - Network Security Expert Series - Cisco Secure Firewall - English
Module 2 - Network Security Expert Series - Cisco Secure Firewall - English
Network security is vital for defending against cyberattacks, ensuring business continuity, and protecting both personal and organizational data from malicious activities.
3:47:36