Unlocking a Seamless Migration from VMware to Nutanix Webinar
44:43
Hear from Cisco and Nutanix experts in this on-demand webinar on critical steps for transitioning from VMware to Nutanix.
Related Videos
In Events
-
Play video Cisco Live Melbourne: Insights from BHP and Cisco Industrial IoT
Cisco Live Melbourne: Insights from BHP and Cisco Industrial IoT
Hear Michelle Fernando, Superintendent OT Networks at BHP and Samuel Pasquier, VP, Product Management, Cisco IloT Networking discuss the latest trends transforming the future of mining.
6:20
-
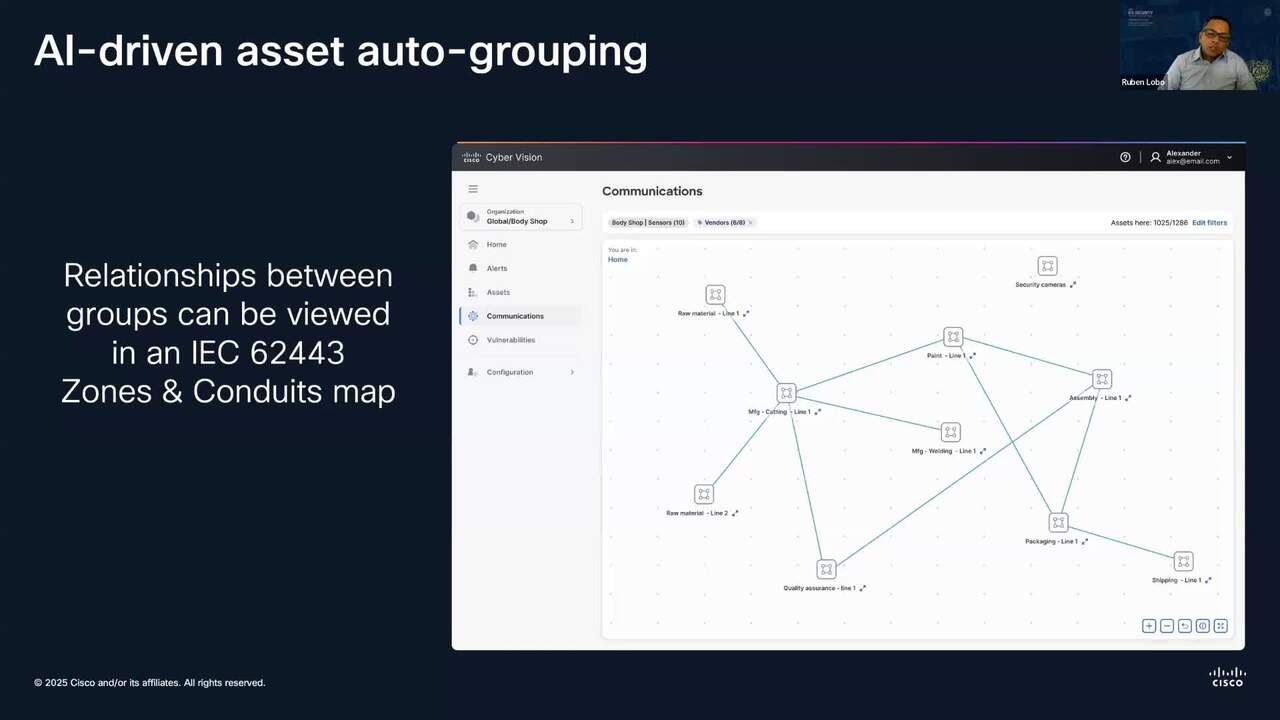
Play video Automating zone segmentation to protect industrial operations
Automating zone segmentation to protect industrial operations
Watch the replay of the SANS ICS Virtual Summit, where Ruben Lobo, Director of Product Management at Cisco IIoT, explores how to build a defensible architecture for critical assets.
31:23
-
Play video Cisco Engage Tech Day Sizzle Reel
Cisco Engage Tech Day Sizzle Reel
Cisco Engage Tech Day Sizzle Reel from Cisco Engage Tech Day Dallas
1:00
-
Play video Cisco Connect 2025 Singapore
Cisco Connect 2025 Singapore
On 31st July 2025, we gathered more than 400 customers, partners & analysts, to join us for a full day of enriching conversations and demos around the AI landscape, innovations and Cisco’s strategy in capturing the opportunities in this new AI era.
1:39
-
Play video Experience Cisco AI Solutions at Gartner IOCS in London
Experience Cisco AI Solutions at Gartner IOCS in London
Mark Maslanka, Managing Director, Cloud & AI at Cisco, previews Gartner IOCS in London! From full-stack infrastructure with NVIDIA to edge solutions that integrate compute, networking, security, storage and observability, this is a can't-miss event.
1:50
-
Play video Fireside chat with Jeetu Patel, Cisco President and CPO, and CNN Senior Reporter Matt Egan - The Catalyst for Driving an Agentic AI Revolution
Fireside chat with Jeetu Patel, Cisco President and CPO, and CNN Senior Reporter Matt Egan - The Catalyst for Driving an Agentic AI Revolution
Cisco’s President and CPO, Jeetu Patel, explores how agentic AI is reshaping security, collaboration, and the workplace. Discover why organizations that embrace this shift will lead the way, and how Cisco is helping them scale with resilience.
18:33