Shift Left Security: How Developers can Assume Responsibility on their Apps
18:44
Cloud applications/microservices architecture require a shift left in responsibilities, both deployments and security aspects.
Related Videos
In DevNet Create 2021
-
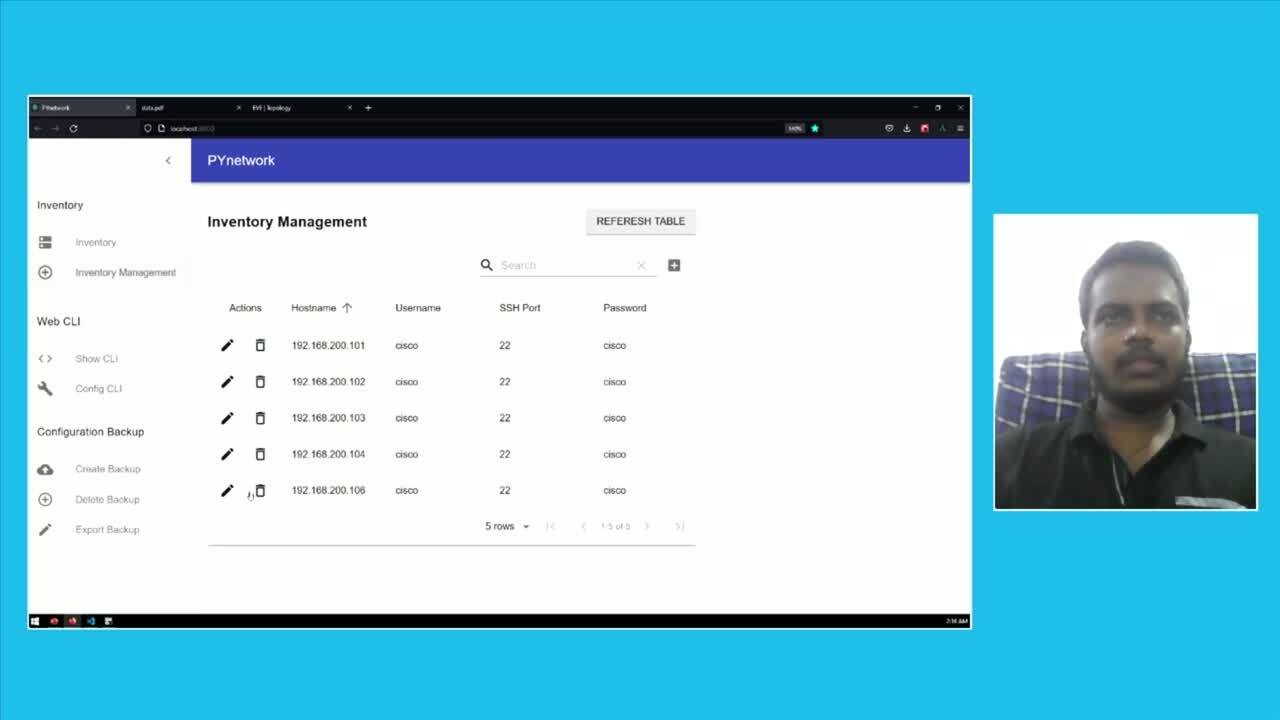
Play video Automate the Network with WEB GUI PYnetwork
Automate the Network with WEB GUI PYnetwork
It is a Web based Network Automation tool, Backend - flask, front-end React and Material UI and database is sqlite.
9:37
-
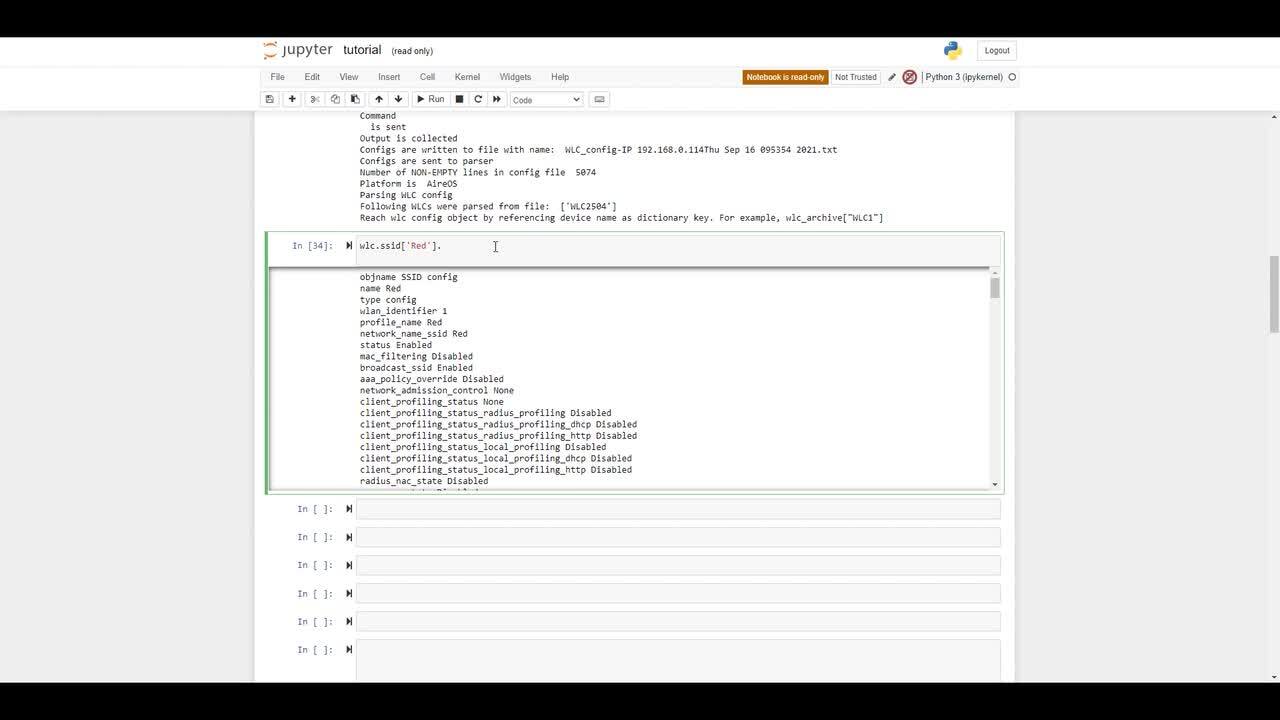
Play video How to Python-ize the data from wireless network
How to Python-ize the data from wireless network
Cisco Wireless LAN Controller configuration files contain a lot of useful information. But basic Python knowledge with the WLC pythonizer tool will allow anyone to reach new heights in configuration analysis and wireless network operational data.
20:53
-
Play video Watch how streaming telemetry, open-source tooling, and APIs turn into an amazing BBQ setup. DevNet Snack Minute Episode 42.
Watch how streaming telemetry, open-source tooling, and APIs turn into an amazing BBQ setup. DevNet Snack Minute Episode 42.
Join Matt and Kareem as they chat with Developer Advocate Quinn Snyder, as he demonstrates using streaming telemetry concepts and open-source tooling, along with some handy APIs, to achieve perfect data-driven outcomes and delicious meal results.
16:46
-
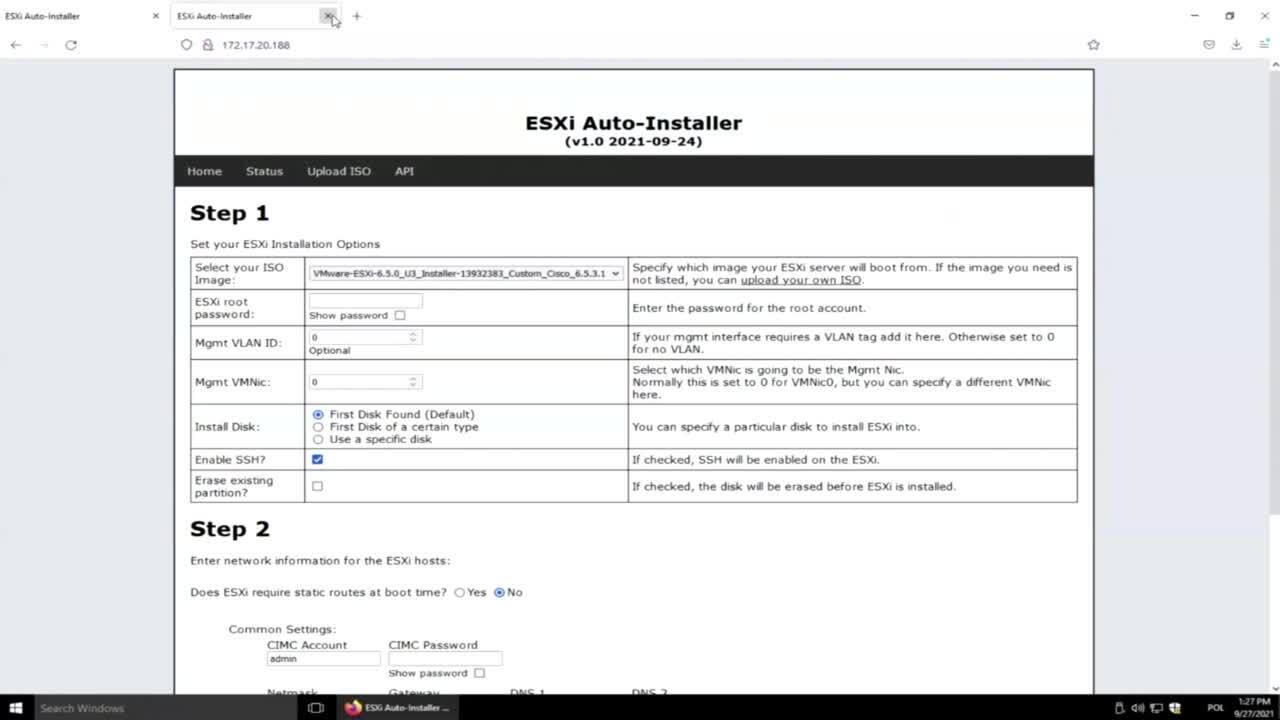
Play video Automated ESXi Installs
Automated ESXi Installs
Ever installed ESXi so many times that yellow console screen is burned into your eyes? Using basic DevNet concepts like Python, a Web Page, and APIs, this code enables mass ESXi deployments on Cisco Platforms without logging into an ESXi console.
8:17
-
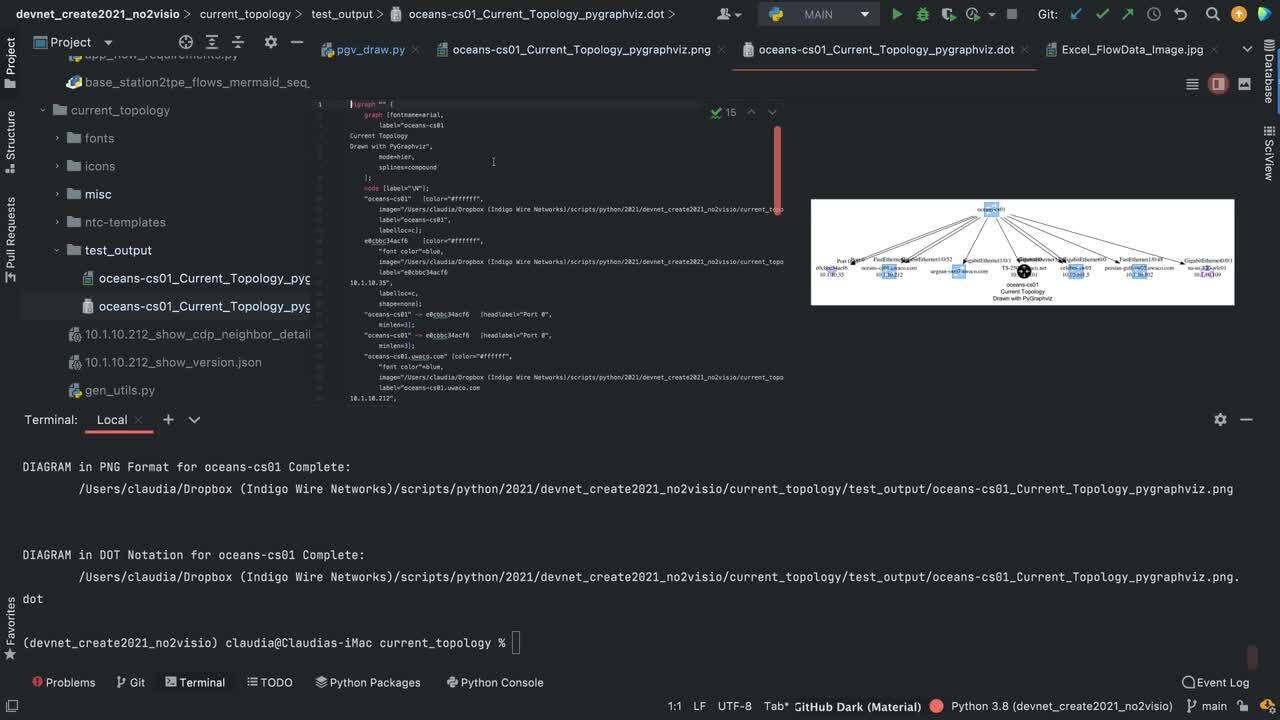
Play video Just say no to Visio
Just say no to Visio
From design documentation to as-builts a good network engineer spends a substantial amount of time drawing. It is time to explore "Documentation as Code" and it make sense to start with diagrams.
18:51
-
Play video Making ice cream with Vanilla ISE
Making ice cream with Vanilla ISE
Vanilla ISE is a simplified UI for Cisco ISE, leveraging ISE's open APIs.
20:10