Configure a Deployment Profile in XDR
2:51
Contributed by: Nayeli Calva This provides the steps to create a Deployment in XDR. Tags: deployment,csc,xdr
Related Videos
For "xdr"
-
Play video #CiscoChat Live - More Intelligent and Confident XDR
#CiscoChat Live - More Intelligent and Confident XDR
In this #CiscoChat, we’ll cover how you can harness more intelligent, more confident extended threat detection and response (XDR) with analytics and automation built in.
47:05
-
Play video Introduction to Cisco XDR webinar
Introduction to Cisco XDR webinar
Learn how Cisco is elevating efficacy and productivity of SecOps around the world with Cisco XDR. We share the Cisco XDR approach to detect and respond faster to the most complex threats, and a product demo that explores features and functionalities
56:17
-
Play video Alphabet Soup: Making Sense of EDR, MEDR, MDR, XDR
Alphabet Soup: Making Sense of EDR, MEDR, MDR, XDR
There are so many acronyms – EDR, MEDR, MDR, XDR, and more – when it comes to cybersecurity, making it harder to choose the right solution for your organization. Join Nirav Shah in this webinar to better understand these solutions.
12:15
-
Play video Enabling Proactive Security Operations
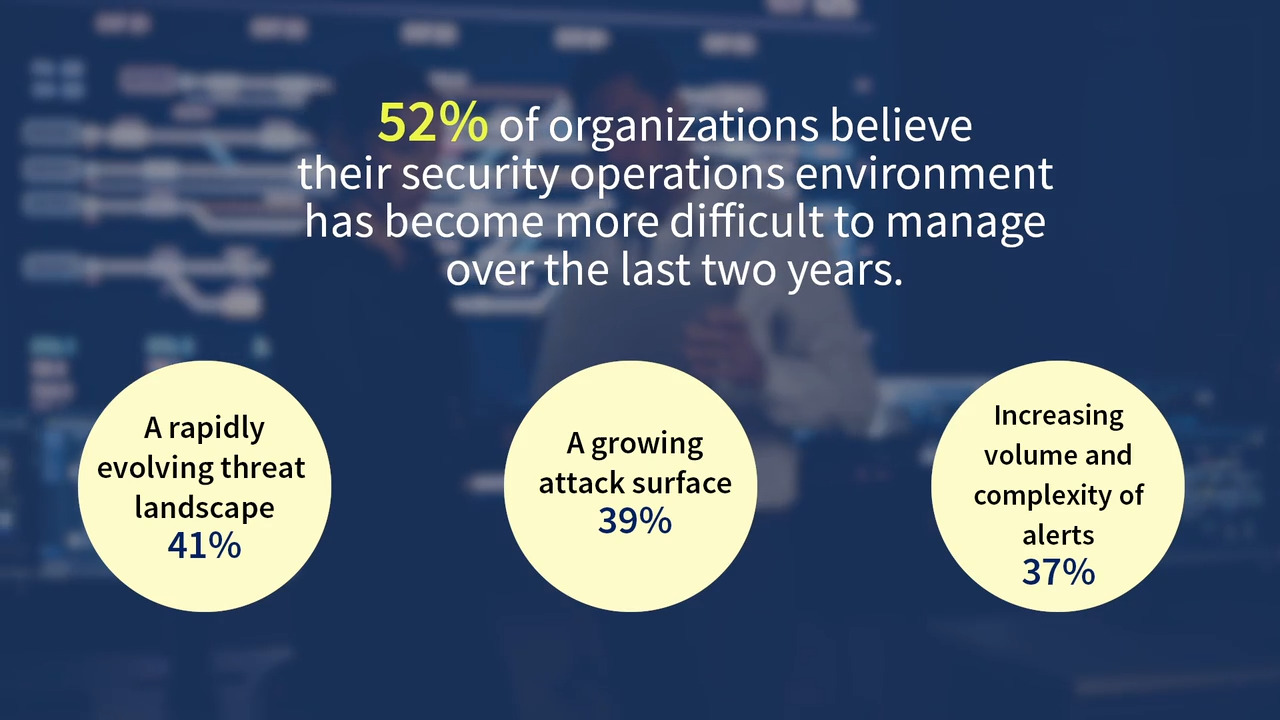
Enabling Proactive Security Operations
Jon Oltsik, ESG Sr. Principal Analyst and Fellow, discusses insights from a recent survey of cybersecurity professionals exploring key trends in security operations. Read the full ESG eBook, SOC Modernization and the Role of XDR, to learn more.
5:09
-
Play video Cisco XDR. Security operations simplified.
Cisco XDR. Security operations simplified.
This video is an overview of the new Cisco XDR extended detection and response solution. With Cisco XDR, your SOC team will detect the most sophisticated threats, act on what truly matters—faster, elevate productivity, and build security resilience.
1:10
-
Play video Beat cyber adversaries at their own game with Cisco XDR
Beat cyber adversaries at their own game with Cisco XDR
With Cisco XDR you’ll be better prepared to take on the most sophisticated cyberattacks, and win. All your telemetry correlated. Detections prioritized and contextualized. Automation shutting them down so fast. A good day for you, a bad day for them.
1:22