Creating a Zero Trust Environment in DoD
4:31
A discussion with Marcos Rogers: Leveraging a Comply to Connect Security Architecture
Related Videos
For "zero trust"
-
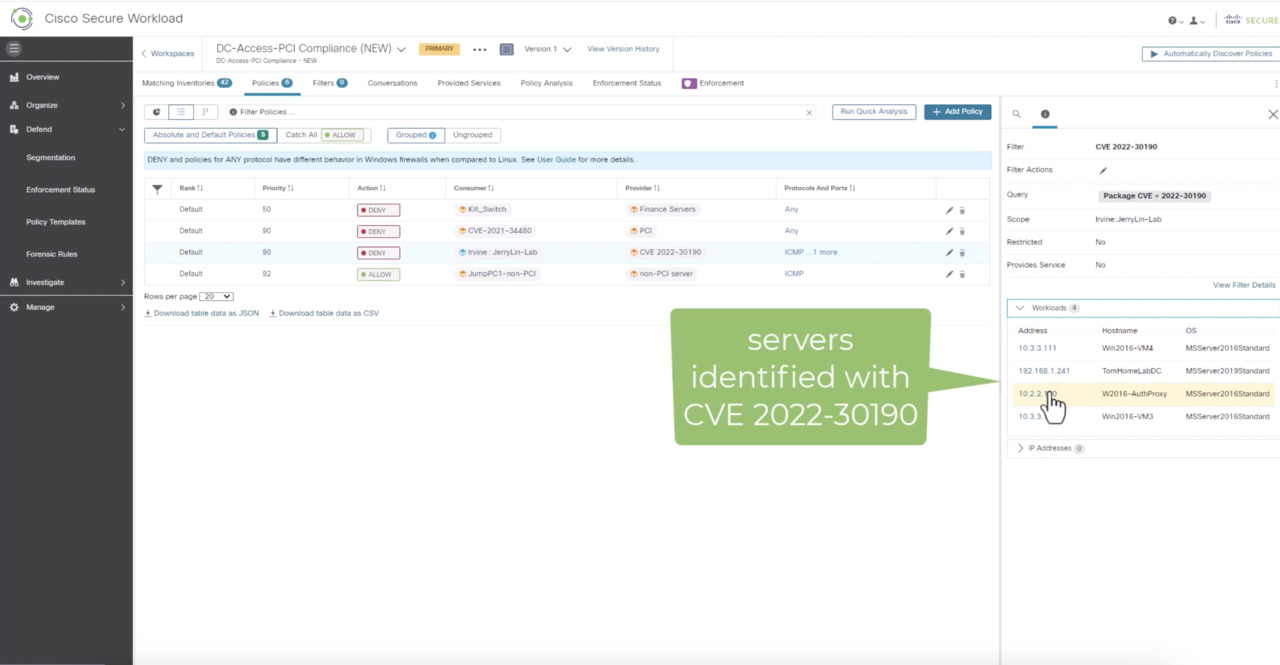
Play video Cisco Zero Trust in Action: Apply micro-segmentation at scale
Cisco Zero Trust in Action: Apply micro-segmentation at scale
This product demo shows how Secure Workload uses vulnerability data to enforce trusted access via micro-segmentation policies. Quite simply, if an app is vulnerable, the policy engine will automatically limit access to it until it can be remediated.
5:36
-
Play video Sara Assicurazioni chose Cisco Secure to implement its Zero Trust strategy
Sara Assicurazioni chose Cisco Secure to implement its Zero Trust strategy
Sara Assicurazioni is a cloud-first digital company serving more than 600 employees and agency offices spread over 1500 points of sale. They improved their threat investigation and remediation efficiency by 20% thanks to Cisco Secure.
3:09
-
Play video Zero Trust at Scale: Cisco’s rollout of Zero Trust
Zero Trust at Scale: Cisco’s rollout of Zero Trust
Following a zero trust model can help reduce risk and protect today's organizations. But how to get started? Hear from Cisco on how we implemented Zero Trust across our entire company in a very short timeframe, while prioritizing user experience.
4:32
-
Play video Cisco Wireless: Zero-Trust How to Demo
Cisco Wireless: Zero-Trust How to Demo
Let's explore rogue management and aWIPS, randomized and changing mac, AI endpoint analytics, and segmentation with Cisco wireless. Learn more at cisco.com/go/wireless
4:15
-
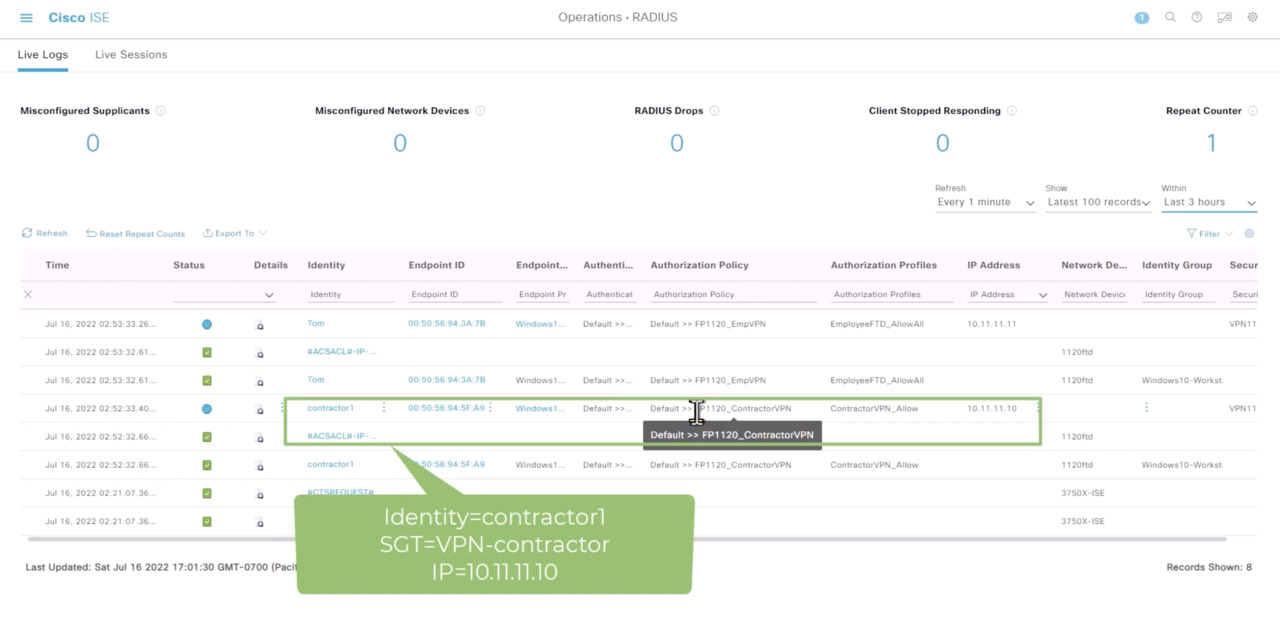
Play video Cisco Zero Trust in Action: Unify access policy across networks and clouds
Cisco Zero Trust in Action: Unify access policy across networks and clouds
This product demo shows how ISE uses Security Group Tags (SGTs) to establish trust and enforce trust-based access based on user type (employee vs. contractor) and then integrates this with the Secure Workload access policy for zero trust security.
7:42
-
Play video Cisco Trusted Access is a practical Zero Trust approach to security
Cisco Trusted Access is a practical Zero Trust approach to security
Learn the meaning of Zero Trust—one name amongst many—advocating for customers to adopt a trust-centric security approach that complements the threat-centric security solutions we’ve already deployed. Cisco’s answer to Zero Trust is our Cisco Trusted
2:50