Cisco Wireless: Zero-Trust How to Demo
4:15
Let's explore rogue management and aWIPS, randomized and changing mac, AI endpoint analytics, and segmentation with Cisco wireless. Learn more at cisco.com/go/wireless
Related Videos
For "zero trust"
-
Play video Sara Assicurazioni chose Cisco Secure to implement its Zero Trust strategy
Sara Assicurazioni chose Cisco Secure to implement its Zero Trust strategy
Sara Assicurazioni is a cloud-first digital company serving more than 600 employees and agency offices spread over 1500 points of sale. They improved their threat investigation and remediation efficiency by 20% thanks to Cisco Secure.
3:09
-
Play video Secure Access, Seamless Experience: LTIMindtree Secures Remote Work at Scale
Secure Access, Seamless Experience: LTIMindtree Secures Remote Work at Scale
Watch how this leading global technology consulting company modernizes their zero trust to boost cyber resilience and improve user experience.
3:13
-
Play video Cisco Trusted Access is a practical Zero Trust approach to security
Cisco Trusted Access is a practical Zero Trust approach to security
Learn the meaning of Zero Trust—one name amongst many—advocating for customers to adopt a trust-centric security approach that complements the threat-centric security solutions we’ve already deployed. Cisco’s answer to Zero Trust is our Cisco Trusted
2:50
-
Play video Cisco Identity Services Engine (ISE) leaps into infrastructure as code with ISE 3.1 from the cloud
Cisco Identity Services Engine (ISE) leaps into infrastructure as code with ISE 3.1 from the cloud
See how provisioning ISE from the cloud enables rapid deployment of network accesses and control services to anywhere, automatically extending policy to build zero trust within the workplace without slowing down the business.
1:43
-
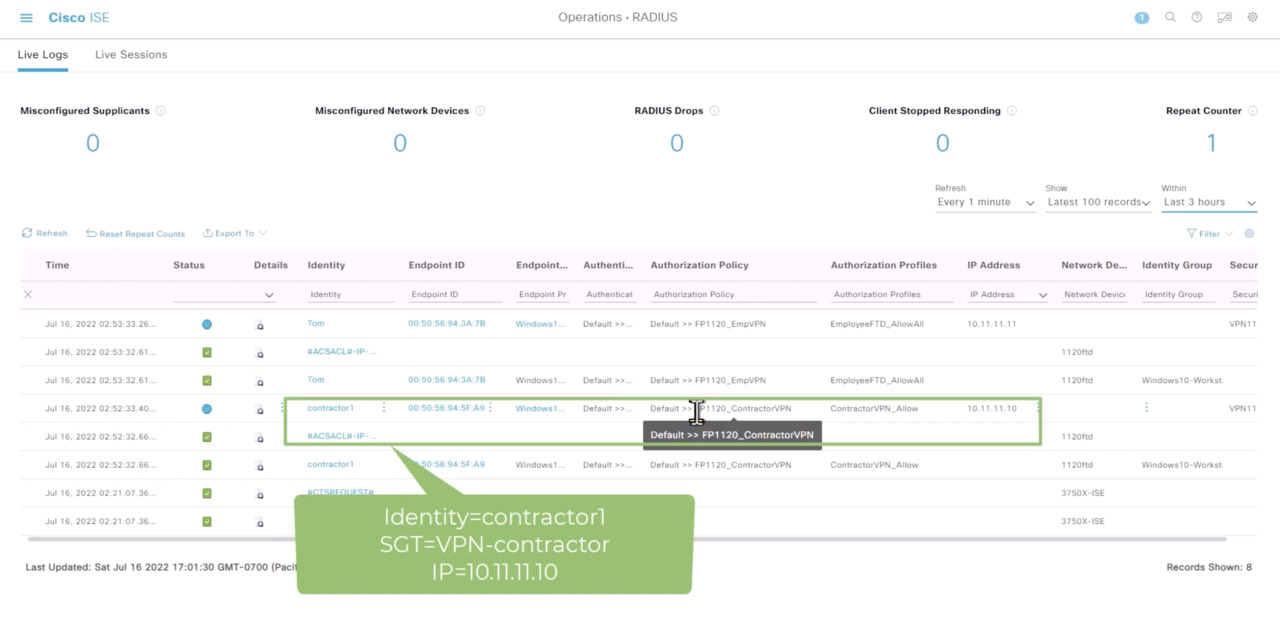
Play video Cisco Zero Trust in Action: Unify access policy across networks and clouds
Cisco Zero Trust in Action: Unify access policy across networks and clouds
This product demo shows how ISE uses Security Group Tags (SGTs) to establish trust and enforce trust-based access based on user type (employee vs. contractor) and then integrates this with the Secure Workload access policy for zero trust security.
7:42
-
Play video ISE 3.0 Demo - Simplifying visibility and control in the zero-trust workplace
ISE 3.0 Demo - Simplifying visibility and control in the zero-trust workplace
ISE 3.0 is here. Take a look at the new UI and see how we are simplifying visibility and compliance with agentless posture and enabling cloud-first strategies. Learn more about ISE: https://www.cisco.com/c/en/us/p
3:48